Telegram Forensics: Getting Started
Introduction
Telegram is one of the world's most popular messaging applications with over 700 million monthly active users. It has evolved from a simple messenger into a comprehensive ecosystem offering features like groups and channels, making it akin to a social media platform. However, not all users and entities on Telegram are legitimate. Those channels and groups are extremely easy to create and delete, and there are cases when they are used to sell illicit goods and run fraudulent activities.
In the context of criminal and cyber investigations, Telegram can hold a wealth of valuable evidence, from users' conversations and activities to potential traces of malicious content. Navigating this data can be challenging, especially for those unfamiliar with the platform.
In this article, we will explore Telegram's features and the devices where its data can be located. Additionally, we will show how to acquire data from Telegram servers with the help of Belkasoft X, a digital forensics and cyber incident response (DFIR) tool designed for extracting and analyzing data from various applications.
Understanding Telegram
In a nutshell, Telegram is a client-server application that stores users' messages and files on its cloud servers. Users can access their Telegram data from multiple devices, including iOS and Android phones and tablets, macOS and Windows computers, or using a web browser on any device.
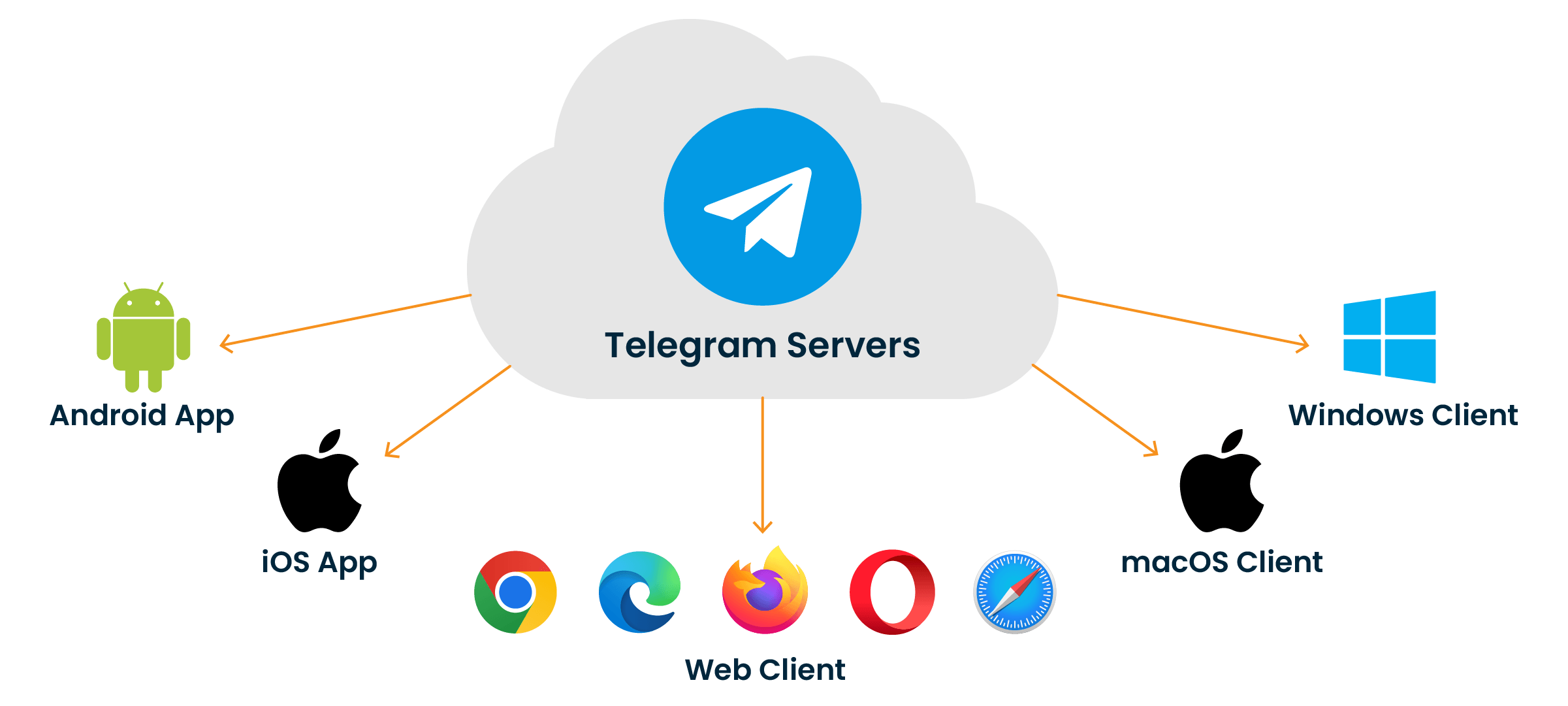
In addition to cloud-stored chats, groups, and channels, Telegram also provides the ability to create "Secret chats" that are only accessible in the clients where they were created. Such chats are also end-to-end encrypted, meaning that the decryption key to the chats exists only on the client devices, while the Telegram server is not involved in their generation.
When creating a Telegram account, users are required to associate it with a phone number that is also subsequently used for authentication. While typically it is a regular mobile number that can be traced back to its owner, some users may opt for services like Fragment, which provides anonymous numbers and accounts.
How to obtain Telegram account data
If you have access to a user's SIM card or eSIM, you can log in to their Telegram account with an authentication code. Note that some users enable two-step verification that also requires a password. If you have the necessary credentials, you can load user data into a Telegram client or create a custom app for this purpose. However, these methods may not be forensically safe as they make it easy to alter user data. The most straightforward way to acquire Telegram cloud data is with a specialized DFIR tool, such as Belkasoft X.
Before you begin, you should note that if a user is logged into their account on any client, Telegram will send the verification code to that client instead of an SMS. It means that you either need to have access to the user's device to get the code or make sure that all user's clients are offline.
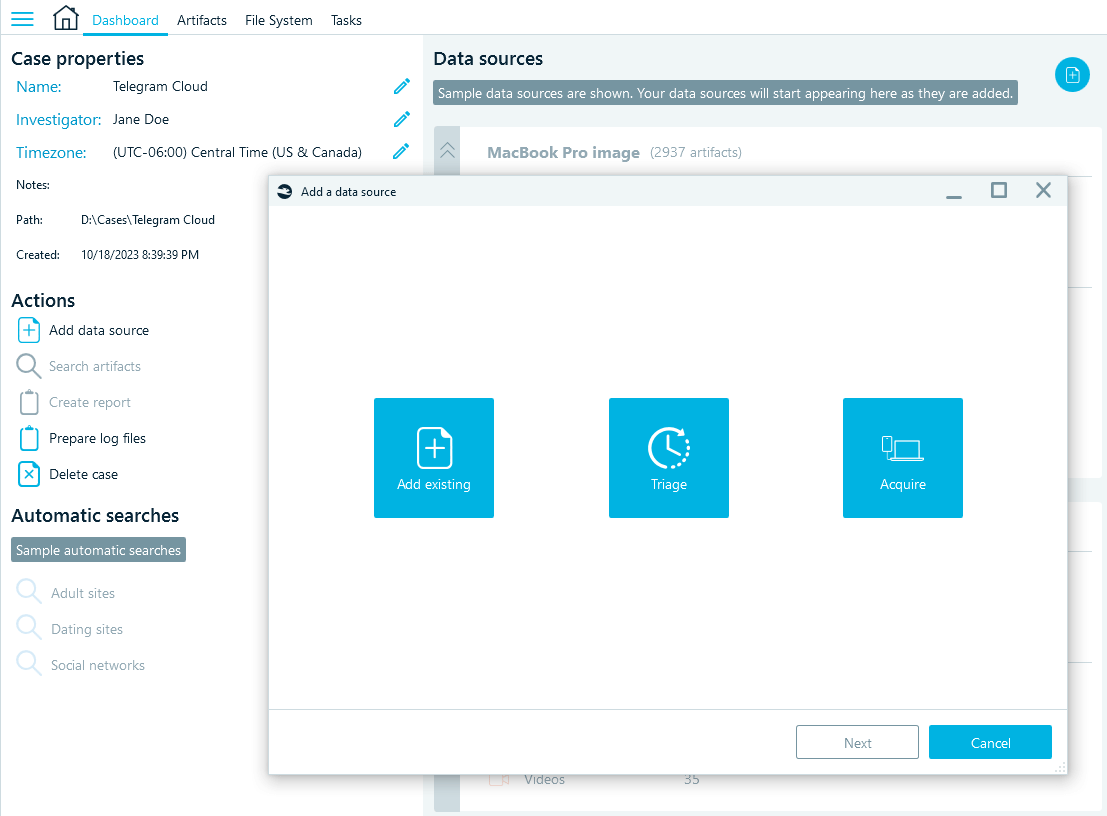
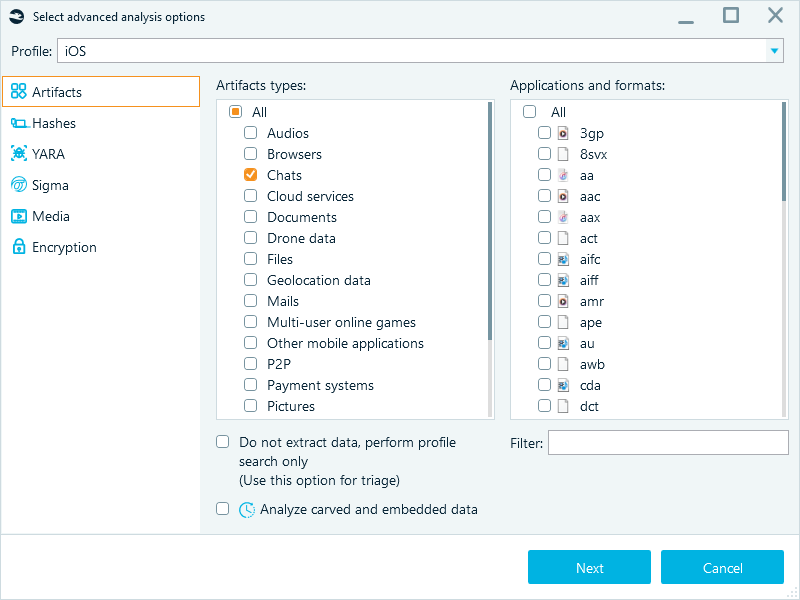
- To start the acquisition, launch Belkasoft X and create a case. Then, begin adding a data source:
- Select Acquire → Cloud → Telegram.
- Enter the phone number of the account you want to acquire. If you have the password for two-step verification, select Yes and provide the password in the below field.
- Select the folder where to save the acquired data and click Start.
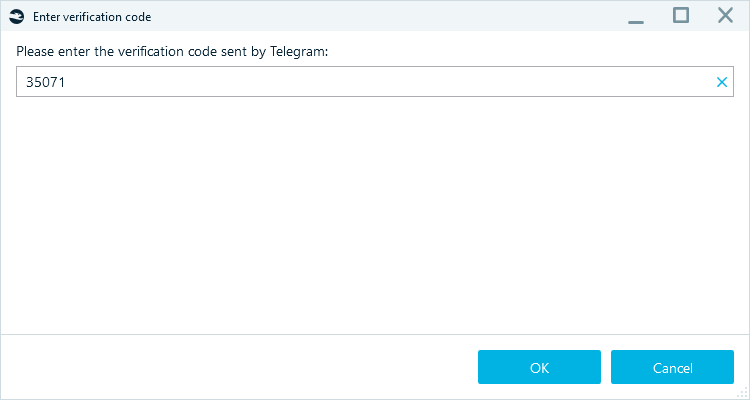
- Next, provide the verification code.
- If the verification is successful, Belkasoft X begins the acquisition. You can check the process status in the "Tasks" window.
- When the acquisition is complete, select the Chats artifact type in the analysis options and run the data source processing.
- The tool analyzes the acquired Telegram data and displays it in the "Artifacts" window:
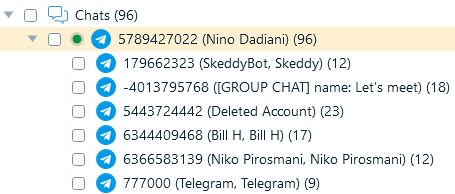
- By default, all messages are displayed in one window. To split them into chats like in clients, right-click the Telegram profile and select Show contacts.
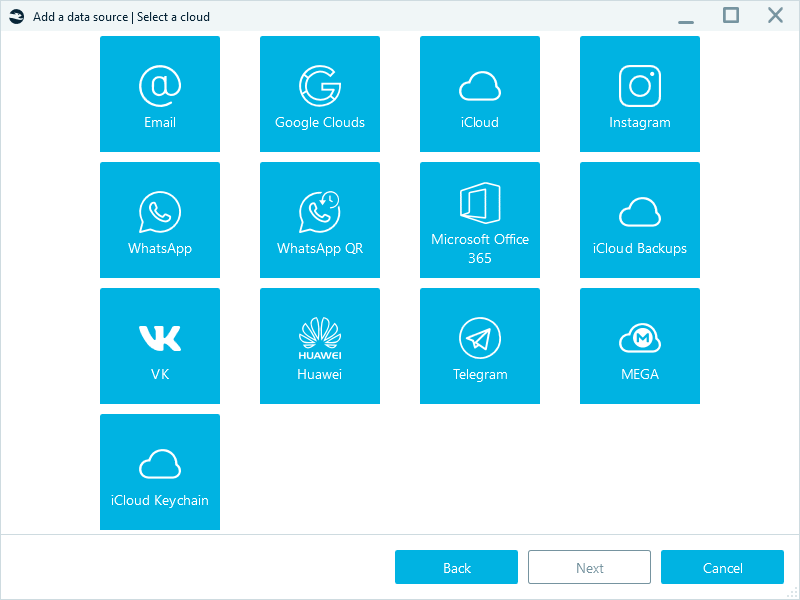

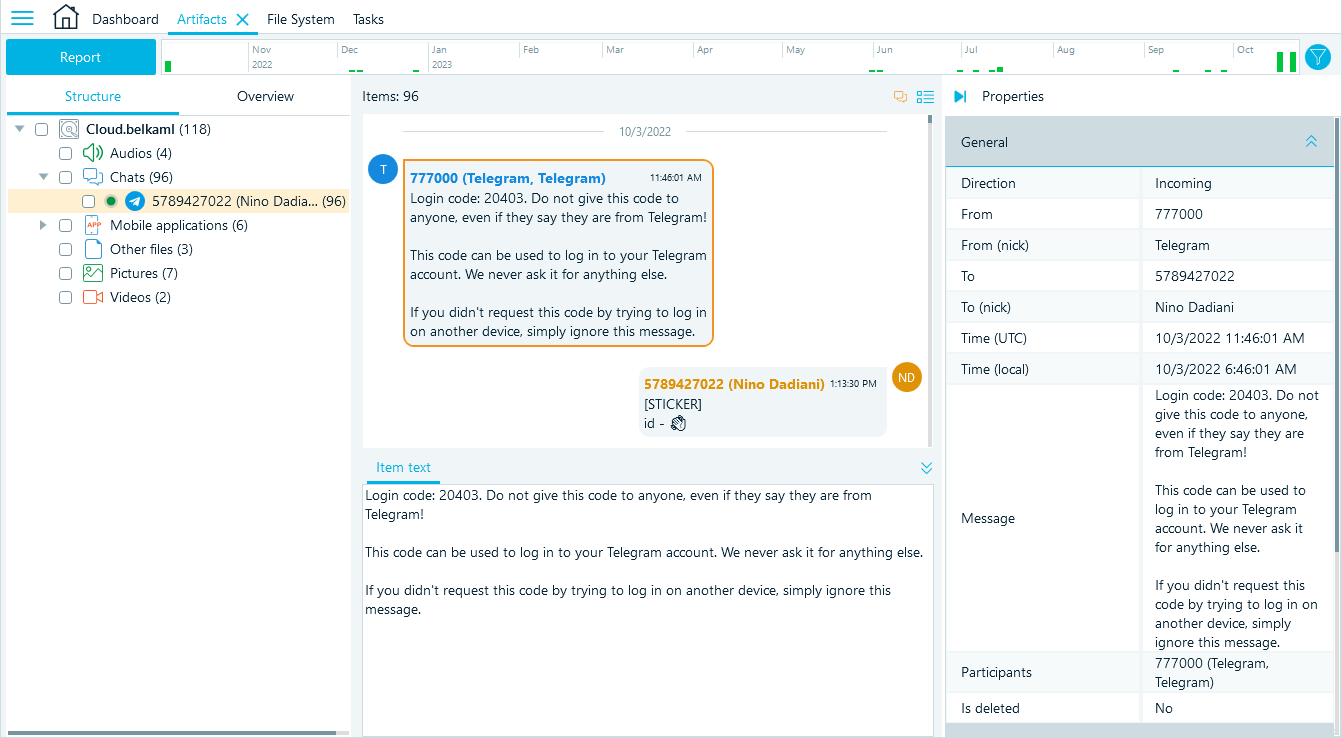
Telegram data types available in the cloud
By analyzing Telegram data, you can learn about the user's connections, communication, and activities. From the cloud, you can typically load such data as:
- One-to-one chats
- Group chats
- Saved messages
Saved messages may be particularly interesting to explore since Telegram features them as "cloud notes," and many people indeed use them as a storage for important information and to share files across devices.
Attached files, such as images (including stickers), video, audio, and documents, are loaded from the cloud together with chat data and can help better understand the conversations and events within the platform.
As you may see, Telegram allows you to acquire a lot of valuable information from the cloud, however, several important components will be missing. Secret chats, as we have explained before, only exist on devices and thus can be acquired from those only, along with user's channels, deleted messages, and message edit history. We will be covering this part of Telegram forensics in our upcoming articles.
Conclusion
Telegram's architecture and authentication mechanisms allow you to obtain account data even without user devices. Such data may include one-to-one and group chats, private notes, and exchanged files. To acquire Telegram cloud data in a forensically sound manner, you can use a specialized digital forensics tool such as Belkasoft X.
While Telegram cloud data provides a lot of valuable data, for a deeper understanding of the user's activities, it is necessary to acquire data directly from their device.
Stay tuned for Belkasoft's articles about Telegram forensics on devices!
