Signal is widely considered to be one of the most secure messaging services. Even Edward Snowden called Signal his favorite messenger app.
While the exact figures for Signal's user base are not publicly known, reports indicate that the application saw 10 million downloads in Google's Play Market in 2020, and another 40 percent of the app's users are on iOS. Signal rivals include messaging applications with larger user databases (like WhatApp, Telegram) and smaller niche messaging applications (like Wickr and Dust).
With the latest investments from Brian Acton, a WhatsApp co-founder, Signal continues to gain momentum and is becoming more popular with security-conscious users, activists, journalists, and lawyers.
The application is even recommended for use in government spaces. In February 2020, European Commission advised its staff to switch to Signal to improve the security of their communications. By 2020, over 30% of news outlets in the U.S., including the New York Times, Washington Post, and Wall Street Journal, use Signal to receive new tips.
The core idea behind Signal is to provide users with the highest levels of anti-surveillance capabilities possible. Unfortunately, such a secured application can also be used by lawbreakers as an entry point for criminal activity.
According to the annual EUROPOL report 'Internet organized crime threat assessment', the following crimes might be perpetrated through instant messengers: online solicitation of children for sexual purposes, terrorist acts launched using an application as the point of communication and dark web marketplaces.
Instant Messaging (IM) applications have the potential to become a rich source of evidence in criminal investigations. Moreover, when dealing with such applications, the information that can be collected in the context of an investigation goes beyond text messages.
Why is it so difficult to decrypt the Signal application?
Digital forensic investigators generally encounter roadblocks when attempting to extract evidence from mobile devices. Specific challenges—such as different operating systems on smartphones, setbacks involving passcode recovery, and other issues—define mobile forensics.
The Signal app is hardly an exception. When dealing with this mobile app as a source of evidence, investigators should try to understand its key security features.
Signal app on iOS uses a keychain to store the decryption key, which makes it difficult to decrypt its databases. It is not an easy venture to extract a keychain, because it means you have to access an iOS device with a method which allows acquiring the so-called 'Full file system' (frequently abbreviated as FFS), or be able to download keychain from iCloud.
What is a keychain?
Keychain is the password manager Apple builds into its devices to store users' passwords, credit card details, Wi-Fi login details, and a host of other important data.
Keychain is the most popular password manager used on iPhones, so keychain extraction is an incredibly important and useful capability for any digital forensic investigator or computer security researcher to have.
The problem here is that there is no official way of retrieving keychain data. It is not extracted as a part of iTunes backup; there is no Apple-approved way to access it.
See our article 'Keychain Extraction in Belkasoft Evidence Center'.
How to extract iOS Signal data with Belkasoft X?
1. Extraction of iTunes or iCloud backups will not help
When investigating Signal conversation history on iPhones, the first idea that comes into one's mind is checking the backups. While the idea might work for some applications like WhatsApp—if the user configured the app to store conversation histories in iCloud and iCloud Drive for iOS backups—it can never work for Signal.
Signal simply does not save chat histories and does not keep its encryption keys in local backups. Users cannot instruct the Signal application to backup their conversations, because Signal developers deliberately left out the required functions (for security reasons). If there is nothing stored on the cloud, then iCloud extraction can never be used to obtain Signal data.
2. Full File System extraction will work!
Since backups and cloud extraction will not work, the other technique requires a full file system extraction.
Belkasoft X acquire a full file system from multiple models of iOS devices through the checkm8-based feature, agent-based full file system acquisition or if a device is jailbroken.
Using Belkasoft X, the basic procedure for an iOS Full File System extraction (with the aim of obtaining Signal data) consists of these steps:
- Identify the iPhone model from which you intend to extract evidence
- If you are dealing with iPhone models starting from iPhone 5S till iPhone X (or iPads with the same SoC) running iOS versions from 12.0 to 15.7.* (or 16 beta, but not release), you may use the checkm8-based acquisition method in Belkasoft X
- For iOS versions 10.3-14.3 and 15.0-15.1.1, you can use agent-based acquisition functions (though we support later iOS versions for this method, we will not extract keychain for them)
- For other iPhone/iPad models or iOS versions, you will have to utilize a relevant jailbreak (if it exists)
- Open Belkasoft X on your PC
- Connect an iPhone to your PC with an original Apple cable through the USB 3.0 port
- Choose the checkm8-based or agent-based acquisition method in Belkasoft X
- For checkm8: Enter recovery mode and then enable DFU mode on the iOS device (see instructions provided by Belkasoft X)
- The iPhone (or iPad) and Belkasoft X will start communicating. The product will apply the corresponding exploit. While acquiring a full file system image, Belkasoft X will also extract the keychain file automatically
- The result of the acquisition is a .tar file, which particularly contains Signal database files and a keychain
- Finally, when the image acquisition process reaches completion, the device will be rebooted (for checkm8), or the agent is deleted. In any case, no traces of an exploit will be left on the device
- You can now start analyzing the acquired image
During the analysis stage, Belkasoft X will extract the Signal encryption key from the keychain and automatically decrypt Signal data. After the iOS full file system is extracted, the 'Passwords' node will appear on the Artifacts window:
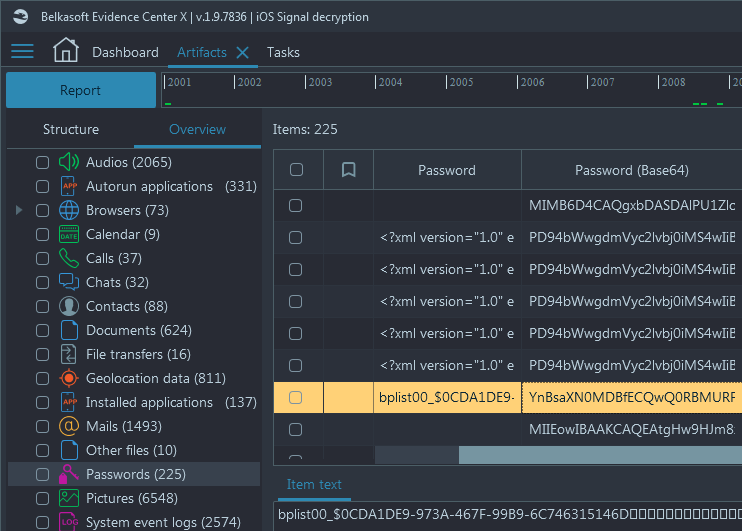
Figure 1. Password node in Belkasoft X
Passwords from the keychain file are stored either as a token or as an original character set in the Password node.
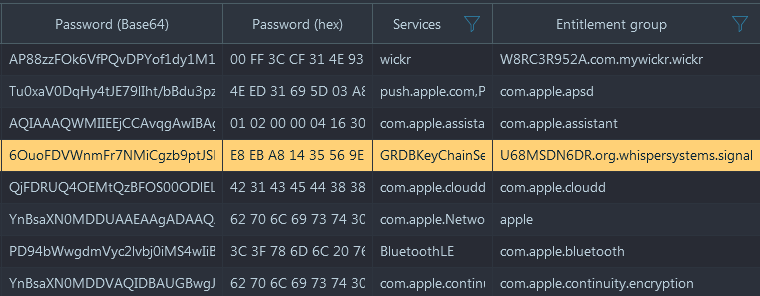
Figure 2. Extracted Signal password
The retrieved data for Signal contains chat history, calls, video, audio messages, shared images and links, and geolocation data, which all fall under the Signal messenger node. The latter is under the Chats node on Artifacts:
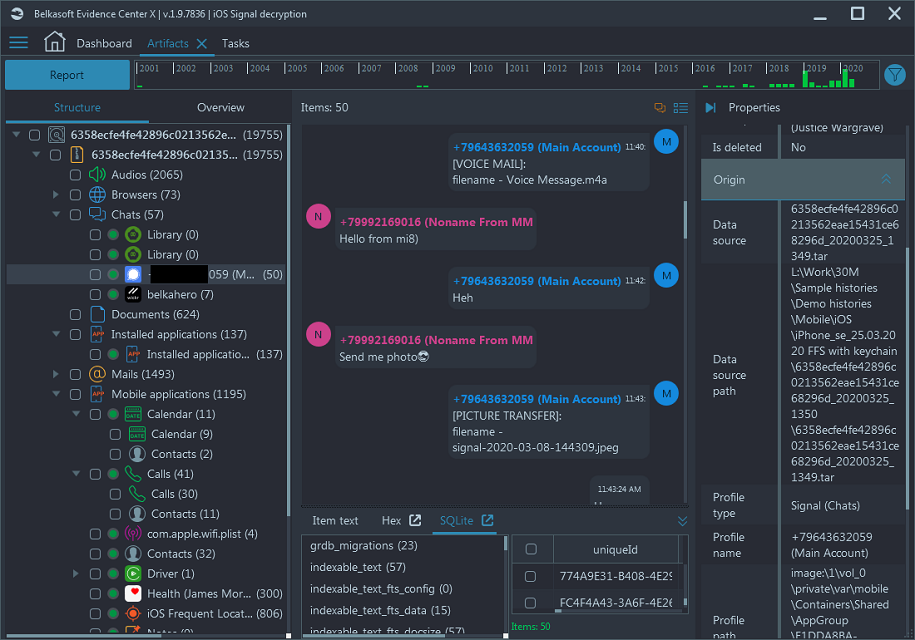
Figure 3. Extracted Signal chat history on Artifacts window of Belkasoft X
Third-party extraction decryption
A separate frequently asked question is 'How do I decrypt Signal data if I have a third-party extraction' (say it, GrayKey or Cellebrite). Since there is no standard way of keeping a keychain in a forensic extraction, the keychain value will not be automatically caught up from a third-party image. However, Belkasoft X allows you to specify Signal keychain value if it fails to automatically find it.
- Go into your third-party image, locate the keychain file. Look for '/private/var/Keychains/keychain-2' or around, though the particular path inside an image is, of course, vendor-dependent
- Find the Signal key which has the id 'org.whispersystems.signal'
- The needed value will look like the following:
ZThlYmE4MTQzNTU2OWU2MTZiZWNkMzIyMGEwY2RiZjY5YjQ5NDhiMzU4MDU0NjUzMzQxYzBhMzRkYmUxOGIwZTAxNGZhNWEyOTUzZjFkODNjMGUyOTI4MGMxM2UxNDk4
This is a base64-encoded value, which, decoded may look like:
e8eba81435569e616becd3220a0cdbf69b4948b358054653341c0a34dbe18b0e014fa5a2953f1d83c0e29280c13e1498
- Belkasoft X will require the value in base64. Under the Tasks window of Belkasoft X, locate the Signal decryption task and click on the 'Enter missing data' button there:
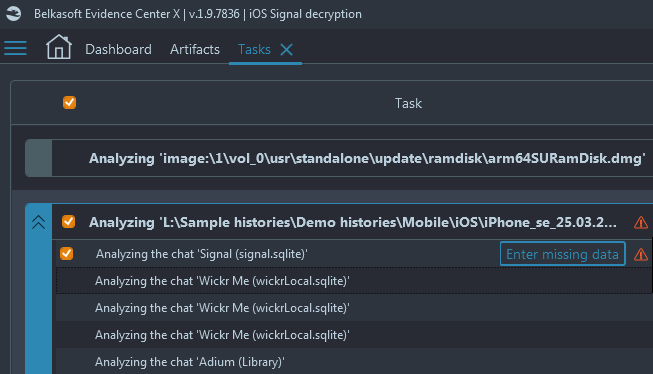
- In the opened window, paste the copied keychain value
- If everything is done correctly, the Signal data will be decrypted and shown under the Artifacts window of Belkasoft X
Conclusion
Signal is an incredibly secure messenger, which is quickly gaining momentum thanks to its impressive anti-surveillance capabilities. For this reason, digital forensic investigators should strive to work with Signal as an evidentiary point.
Signal chat history is not stored in the standard iTunes backup. Its database on an iOS device is well-encrypted using a key stored within the keychain. This is why you cannot decrypt Signal using an iTunes backup or even if you have a Signal database without a decryption key from a keychain.
To successfully decrypt the iOS Signal application, you need a full file system image and keychain. Methods to extract both items vary for different iPhone/iPad models and iOS versions installed and include checkm8, agent-based and jailbreak-based acquisitions.
Belkasoft X supports all of the above-mentioned methods and if an image is acquired with the help of this product, Signal data will be decrypted automatically by the tool. For third-party extractions, Belkasoft X allows you to enter a Signal decryption key which you have to manually locate in a keychain file and copy to the product.
About Belkasoft X
Belkasoft X is a world-renowned tool used by thousands of customers for conducting computer, mobile and cloud forensic investigations. In the previous years, Belkasoft X was pronounced top-3 DFIR commercial tool per Forensic 4:cast Awards, being nominated to the finals of this prestigious competition 4 times out of 5 latest years (2018, 2020, 2021, and 2022).
Belkasoft X can automatically acquire, extract, and analyze evidence from a wide range of sources, including mobile phones, tablets, computers, drones, cloud, memory files and dumps.
