Windows Registry Forensics: Analysis Techniques
The Windows registry is a hierarchical database containing settings and choices for the operating system, hardware components, and installed programs.
Although users rarely interact with the registry, actions like installing or running software, connecting external devices, or changing settings, leave traces. These traces can provide insights into system usage and user behavior in digital forensics and incident response investigations.
The previous article explained the Windows registry structure, its significance, and the specifics of Windows forensic analysis. Following up, here we will review the following practical aspects of Windows registry forensics:
Read on to uncover practical tips for forensic analysis of the Windows registry. We will explore notable Windows registry artifacts for Windows forensics and review how you can analyze them with Belkasoft X.
Analyzing the registry
You can analyze the Windows registry through live system access or inspect a copy of system data offline. The latter is widely regarded as the de facto standard in forensics because it allows you to preserve evidence integrity.
Using Belkasoft X
Digital forensics software like Belkasoft X offers a range of capabilities to extract, parse, and correlate registry data:
- Artifact view: When you add a computer image or collected registry hives as a data source to Belkasoft X, the software extracts key forensic artifacts from the registry, including USB device history, startup entries, time zone settings, and more. We will explore these notable registry artifacts in detail later in this article.
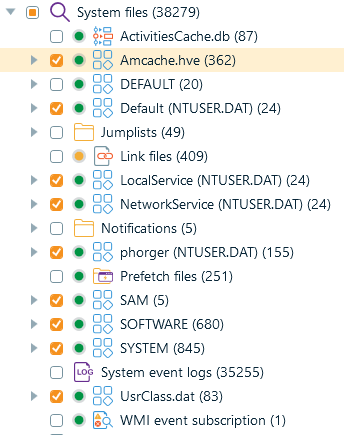
Registry artifacts parsed after drive acquisition in Belkasoft X
- Registry viewer: Open individual hive files for examination. You can use Belkasoft's article on registry structure and storage as a reference for locating hive files in a computer image file system.
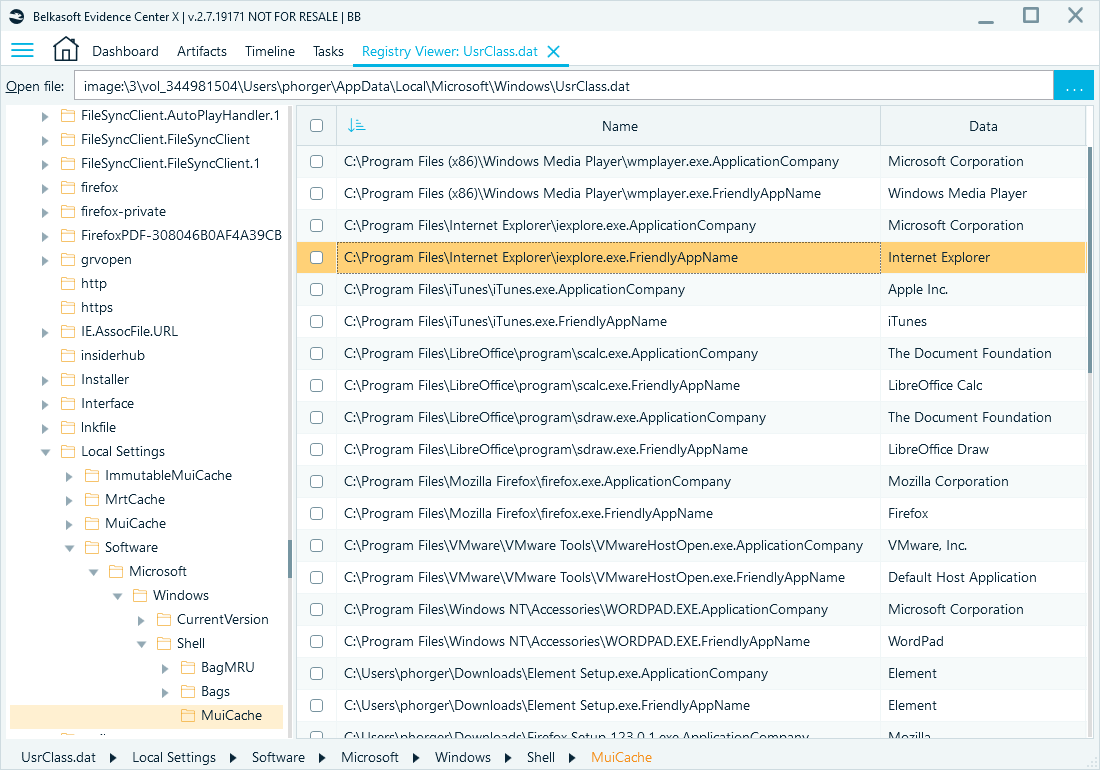
Reviewing the UsrClass.dat file using Registry Viewer in Belkasoft X
If live analysis is necessary—for instance, during active incident response—the recommended approach is to collect registry hive files using safe, system-native methods (such as reg save or Volume Shadow Copies), and then import these files into Belkasoft X on a dedicated forensic workstation.
Using RegEdit
The Windows Registry Editor (RegEdit), a native registry editing tool, allows you to navigate registry records on a live machine and also load hive files under the HKEY_LOCAL_MACHINE or HKEY_USERS root keys to inspect extracted hives offline on another system.
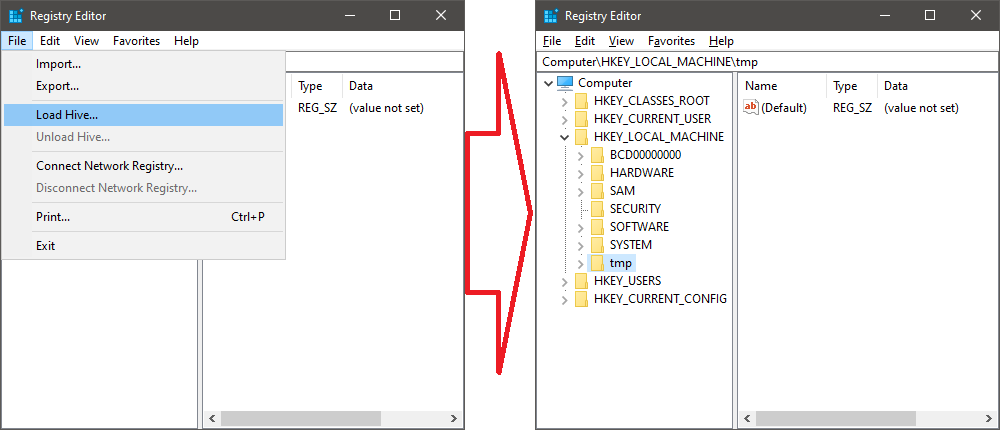
Importing external hive data into RegEdit
RegEdit is a handy built-in tool for viewing and making changes to the Windows registry, but it comes with a few limitations for forensic analysis:
- Manual process: Loading and analyzing hives in RegEdit requires manual operations, which can be time-consuming and error-prone.
- Limited reporting: RegEdit offers basic export options but lacks advanced reporting features for generating detailed analysis reports.
Using command-line utilities
Command-line tools like PowerShell provide flexibility and automation for querying and extracting registry data, which makes them useful for large-scale forensic investigations. Unlike GUI-based tools, they allow scripting, batch processing, and remote registry analysis.
Here are some commonly used PowerShell commands for registry examination:
- Get-Item: Retrieves specific registry keys and their values. This command can be used to quickly extract relevant artifacts. For example, the below command retrieves startup entries:
Get-Item -Path "HKLM:\Software\Microsoft\Windows\CurrentVersion\Run" - Get-ChildItem: Lists all subkeys within a specified registry path, allowing for a broader examination of registry structures. For instance, the following command displays installed services:
Get-ChildItem -Path "HKLM:\SYSTEM\CurrentControlSet\Services" - Reg.exe: A command-line tool to export registry subkeys into .reg files or dump registry hives. For instance, the following command exports the SAM hive, containing Windows account information, to the specified folder:
reg export HKLM\SAM C:\Forensics\SAM.reg /y
Examining the live system with RegEdit or command-line tools can alter evidence and compromise the integrity of the investigation. When possible, prioritize offline analysis methods to ensure the highest level of forensic soundness.
Key forensic artifacts in the registry
Sifting through all of the registry nodes is mind-boggling, especially since the registry structure presented in Registry Editor does not precisely replicate its actual storage structure.
Let us explore a few forensically interesting artifacts you can find in the Windows registry when analyzing it with Belkasoft X.
User accounts
The SOFTWARE hive, contains domain and local user profile details, including SID-to-profile path mappings and profile status.
Registry path: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList.
Following this path, you will see keys named by SIDs. Each key includes values such as ProfileImagePath (the user's profile path) and State. The State value of 0 typically indicates an active user profile. Non-zero values may indicate inactive or corrupted profiles.
Belkasoft X artifact tree path: System files → SOFTWARE → Windows → User name and Sid list.
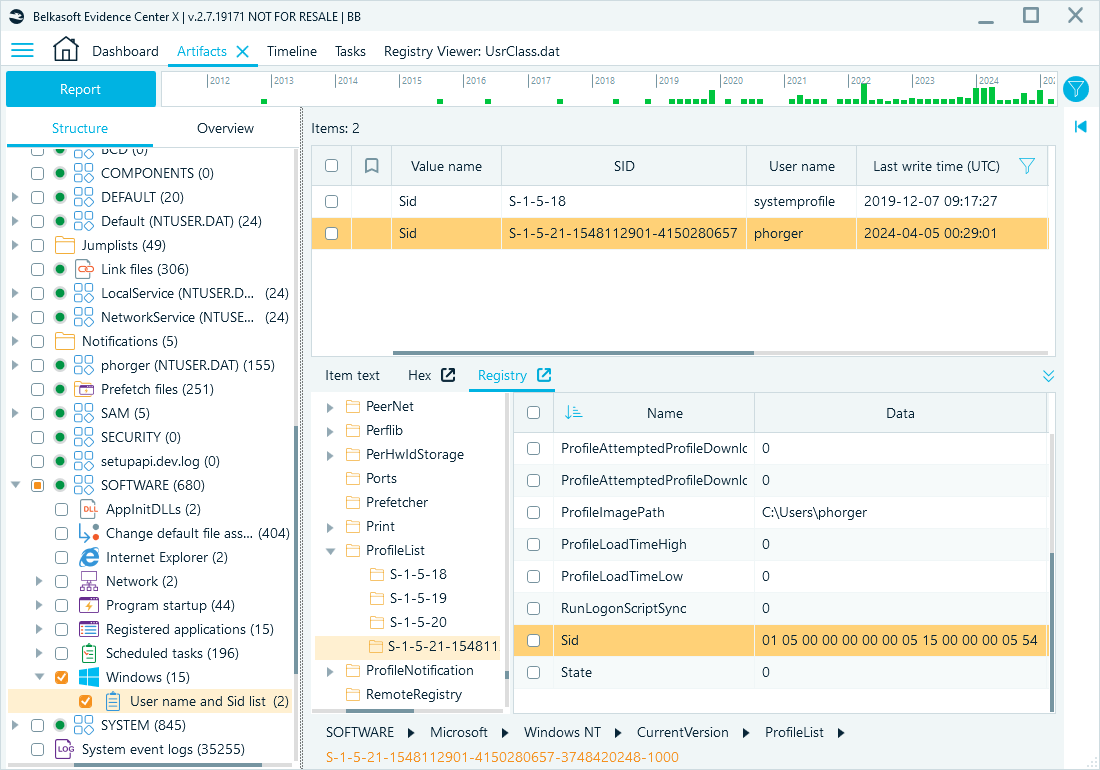
User profile data from the SOFTWARE hive in Belkasoft X
The SAM hive stores security information about local user accounts, including logon counts, password change dates, password hashes, and more. This data can help investigate local account security and detect unauthorized access or suspicious activity.
Registry path: HKEY_LOCAL_MACHINE\SAM\Domains\Account\Users
Belkasoft X artifact tree path: System files → SAM → Windows → Windows accounts
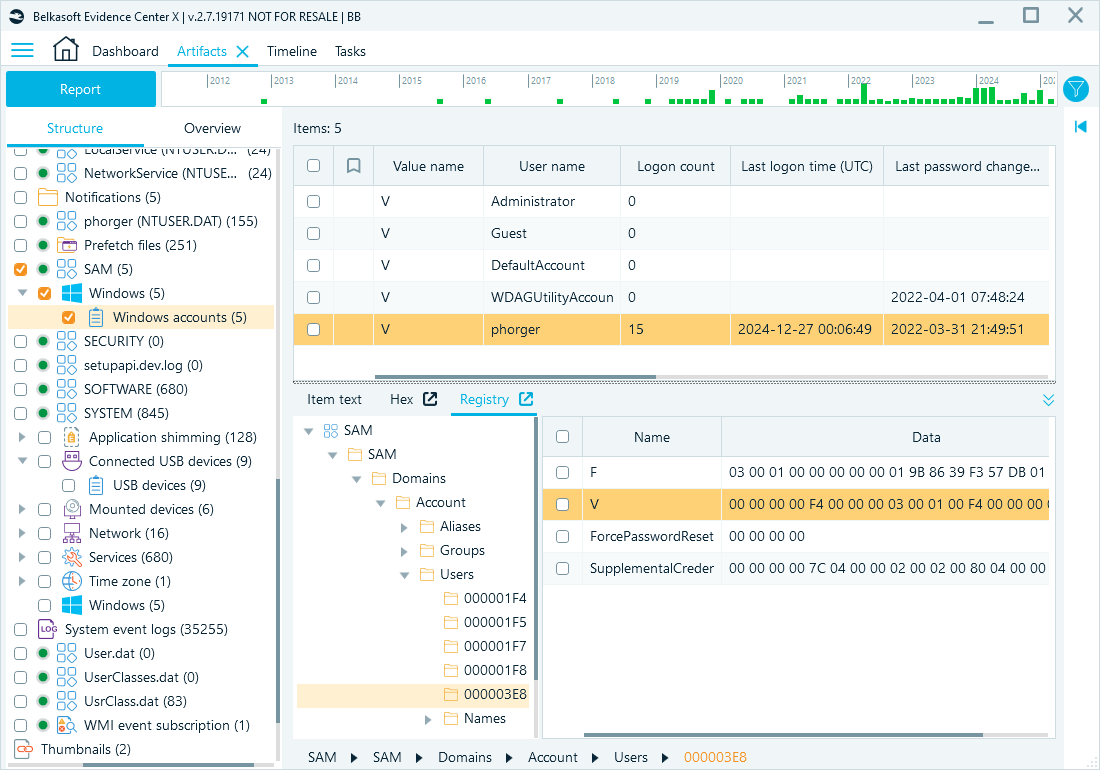
User data from the SAM hive in Belkasoft X
Alt Text: Window with SAM hive opened with Registry Viewer in Belkasoft X
USB device connections
The SYSTEM hive stores details about connected devices: their serial numbers, types, and connection timestamps.
Registry paths (may be unavailable if no associated records were created):
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\USB: Contains records of all USB devices recognized by the system, including input devices, hubs, and peripherals.
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\USBSTOR: Specifically tracks USB storage devices, such as external hard drives and USB flash drives.
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\HID: Stores information on Human Interface Devices (HID), such as keyboards, mice, and game controllers.
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\SCSI: Logs details for devices interfacing via the SCSI protocol, which includes internal drives, virtual drives, and certain external storage devices.
Belkasoft X artifact tree path: System files → SYSTEM → Connected USB devices → USB devices
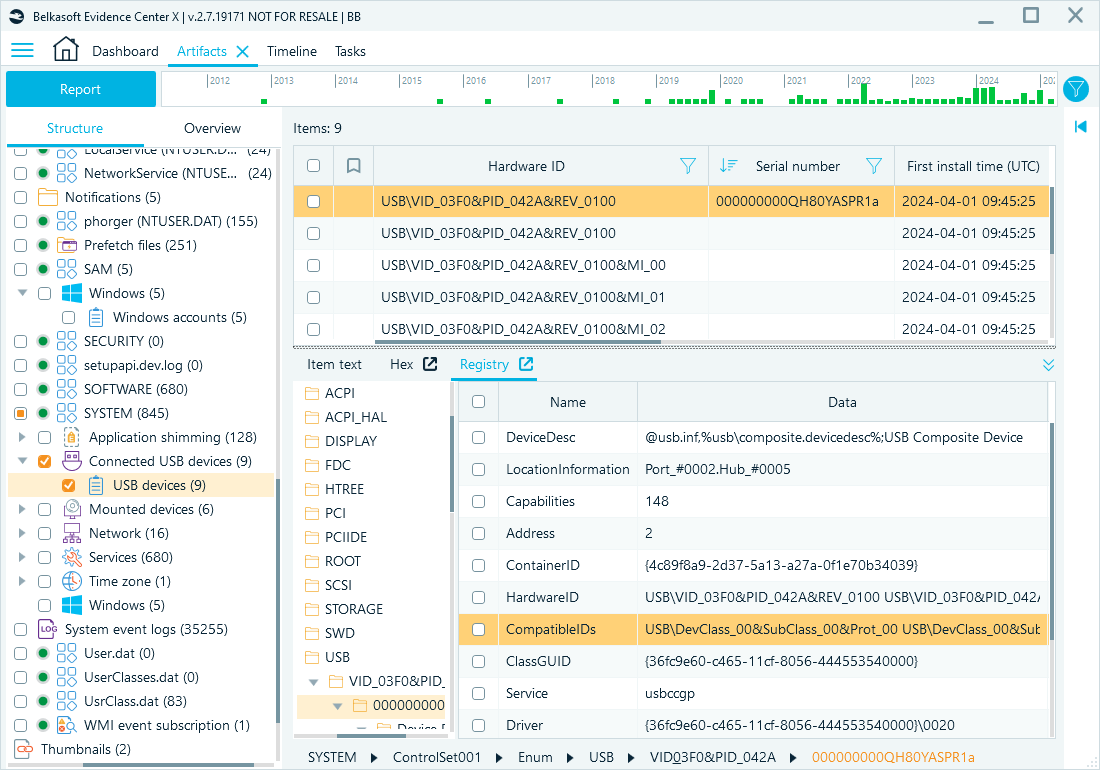
USB devices review in Belkasoft X
Device properties can help you determine:
- Device identity:
- HardwareID: Reveals the vendor (VID_03F0 for HP) and product (PID_042A), which will help determine the exact device model.
- ContainerID: A unique identifier for the device that helps track this device across different ports and sessions.
- Connection details:
- LocationInformation: Specifies the physical port and hub number, helping determine which port the device was plugged into.
- Address: A dynamically assigned USB address helps reconstruct connection order.
- Device class and function:
- ClassGUID: Identifies the device class, indicating whether it is a mass storage device, human interface device (HID), or other type. For example, {36fc9e60-c465-11cf-8056-444553540000} corresponds to USB controllers.
- Service: The driver service associated with the device. For instance, the service name usbccgp (USB Generic Parent Driver) indicates a composite USB device that may contain multiple functions, such as a keyboard and storage.
Note that since the CurrentControlSet key is a symbolic link, Belkasoft X parses and displays data from the key wherethe actual records are stored. The control set in use is determined by the HKEY_LOCAL_MACHINE\SYSTEM\Select key.
Mounted devices
Mounted device records stored in the SYSTEM hive include drive letters and corresponding device paths or volume identifiers. These artifacts help reconstruct storage media usage.
Registry path: HKEY_LOCAL_MACHINE\SYSTEM\MountedDevices
Belkasoft X artifact tree path: System files → SYSTEM → Mounted devices → Devices
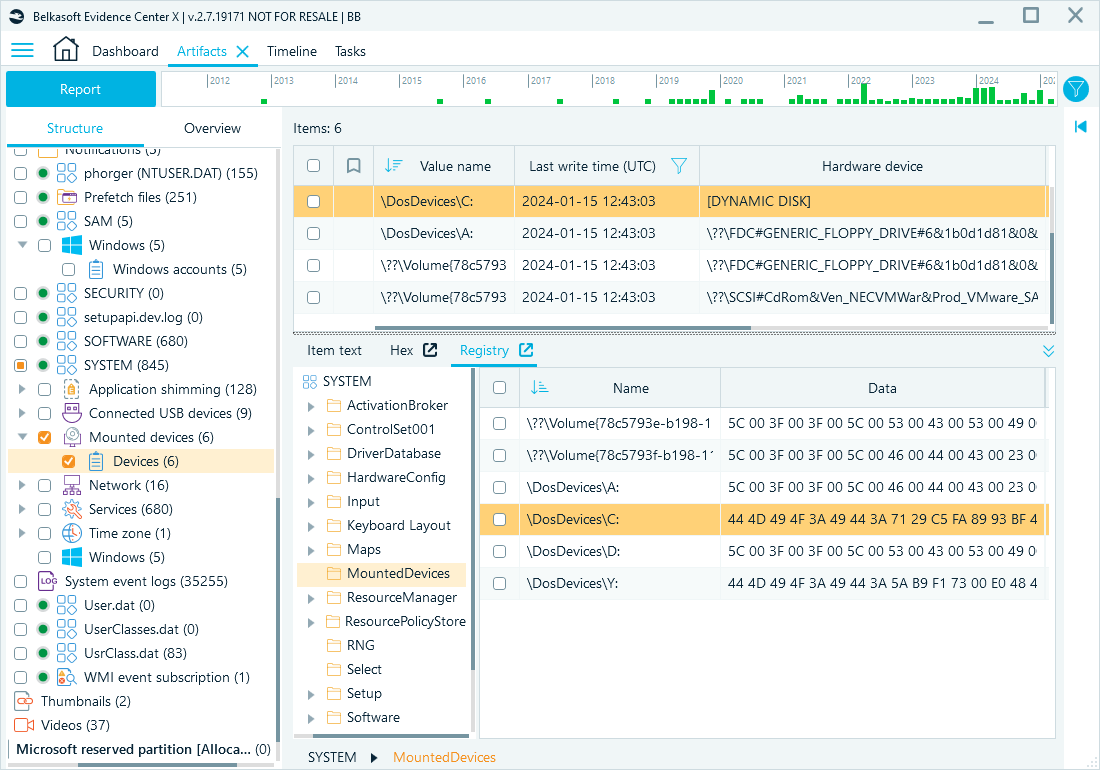
Reviewing mounted devices in Belkasoft X
Time zone settings
Time zone configurations in the SYSTEM hive can align event timestamps with user activities, aiding in timeline analysis. Time zone information helps correlate timestamps across logs, events, and user activity timelines, especially when analyzing systems that have changed locations.
Registry path: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\TimeZoneInformation
Belkasoft X artifact tree path: System files → SYSTEM → Time zone → Time zone
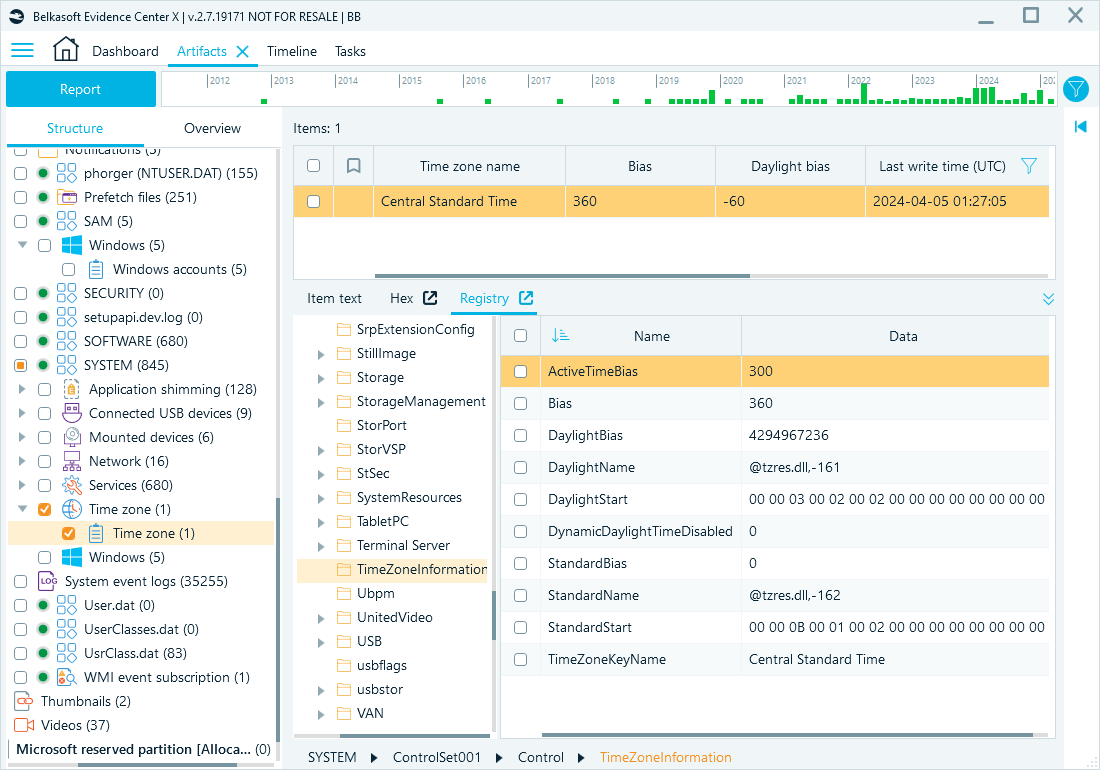
Time zone information review in Belkasoft X.
Services
The SYSTEM hive also records installed and configured services, including startup types and parameters. Windows services, stored in this hive, define what background processes run automatically or on demand. These entries can help identify active services, misconfigurations, or malicious persistence mechanisms.
Registry path: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services
Belkasoft X artifact tree path: System files → SYSTEM → Services → Services
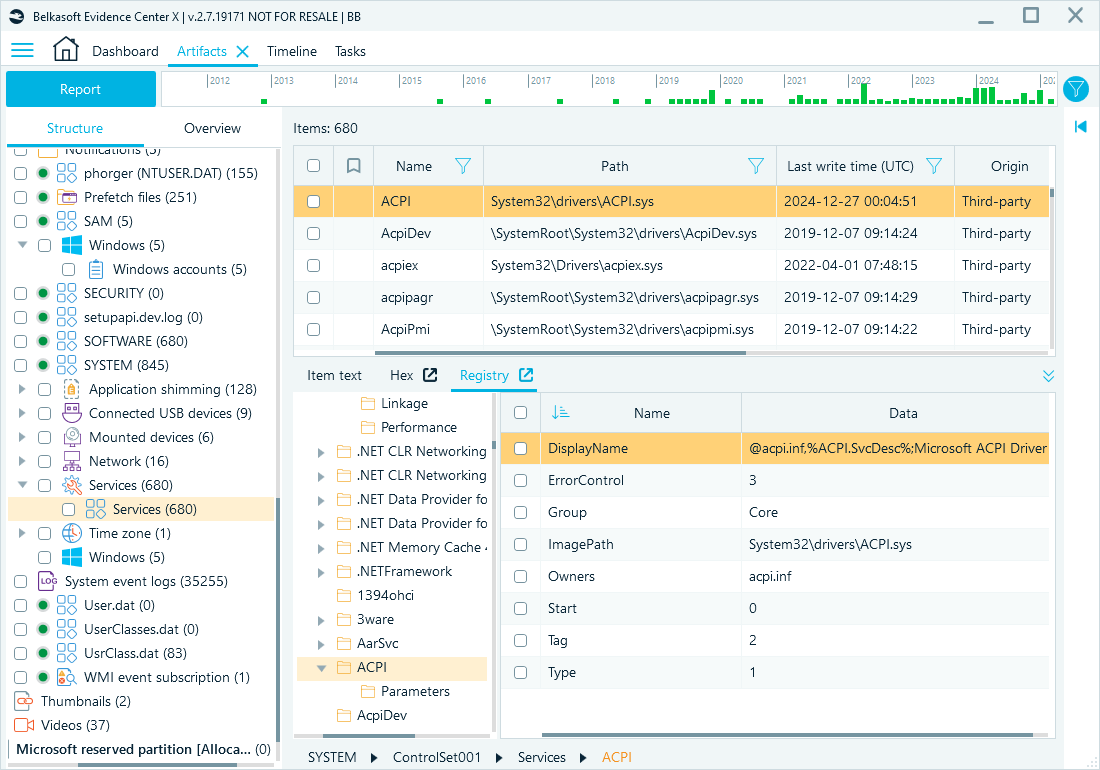
Reviewing services in Belkasoft X
TCP/IP configurations
Network settings, such as IP addresses, DNS servers, and gateways, are stored in the SYSTEM hive. These details might shed some light on network activity and device connections.
Registry path: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters
Belkasoft X artifact tree path: System files → SYSTEM → Network → TCP/IP Configuration
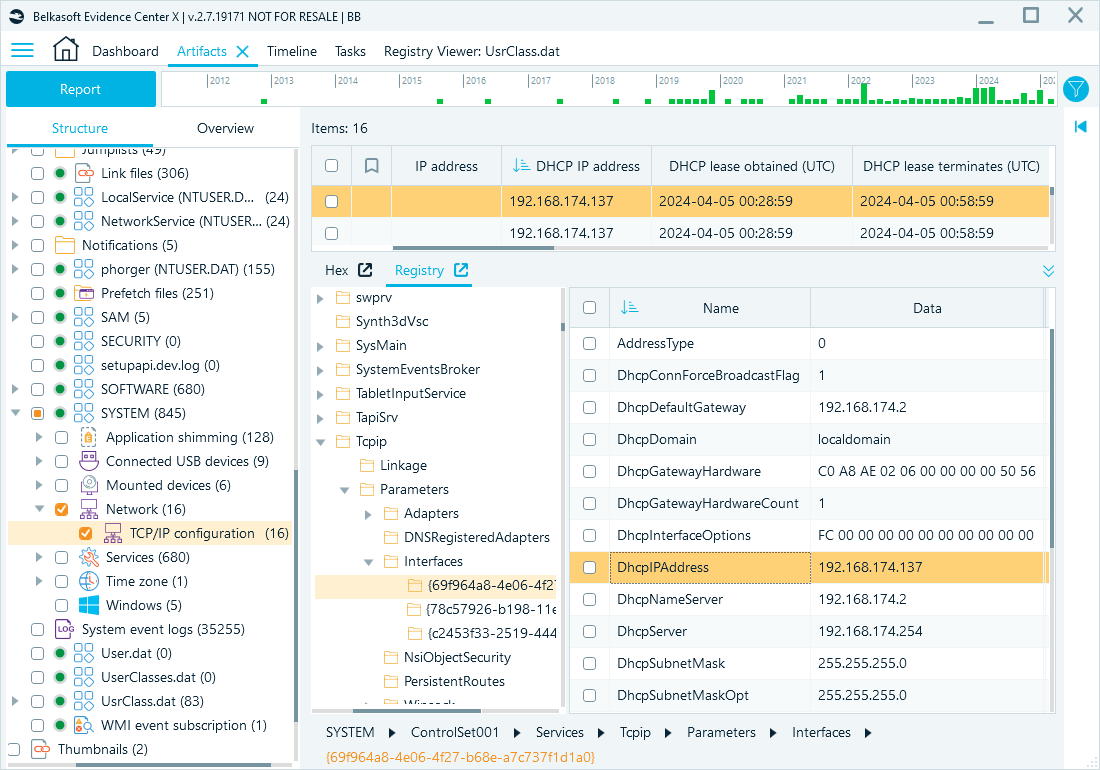
TCP/IP configuration in Belkasoft X
Program startup entries
Startup program configurations, logged in the SOFTWARE and NTUSER.DAT hives, can reveal persistence mechanisms or unauthorized software.
Registry paths:
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Belkasoft X artifact tree: System files → SOFTWARE→ Program startup → Programs
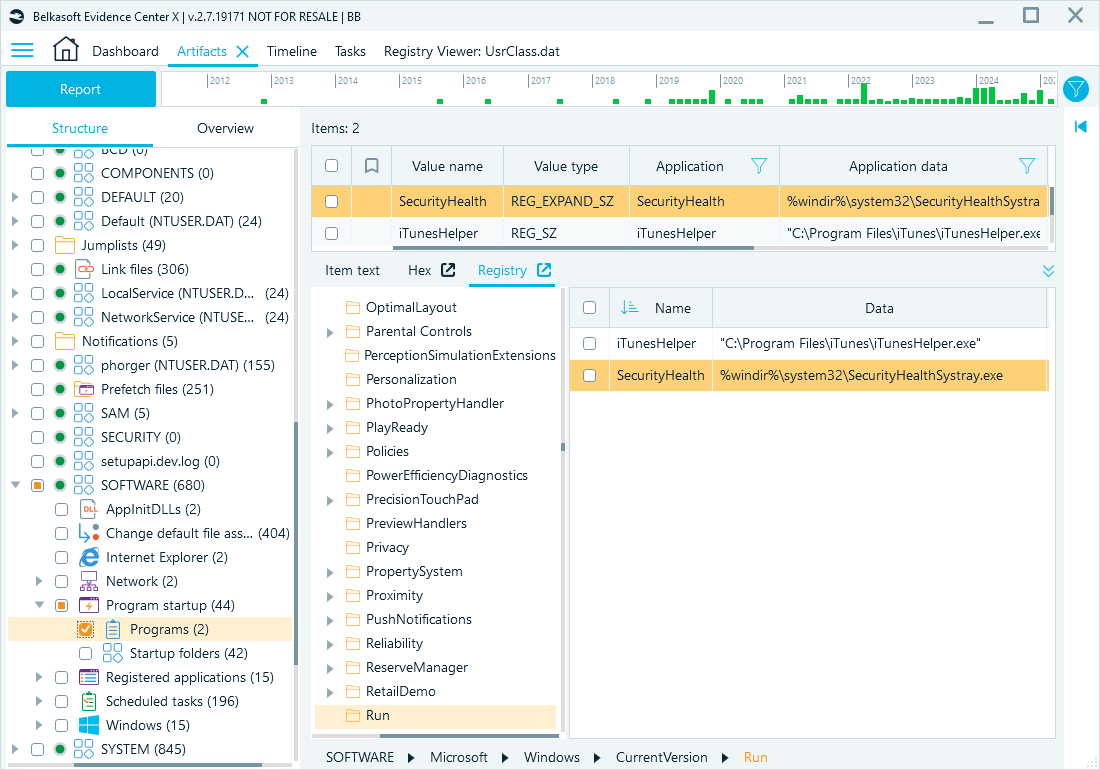
Startup settings in Belkasoft X
Scheduled tasks
Scheduled task configurations, stored in the SOFTWARE hive, provide insight into legitimate and malicious task triggers and actions. Tasks created or modified around a suspicious event timeframe require closer attention.
Registry path: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks
Belkasoft X artifact tree: System files → SOFTWARE→ Scheduled tasks → Tasks
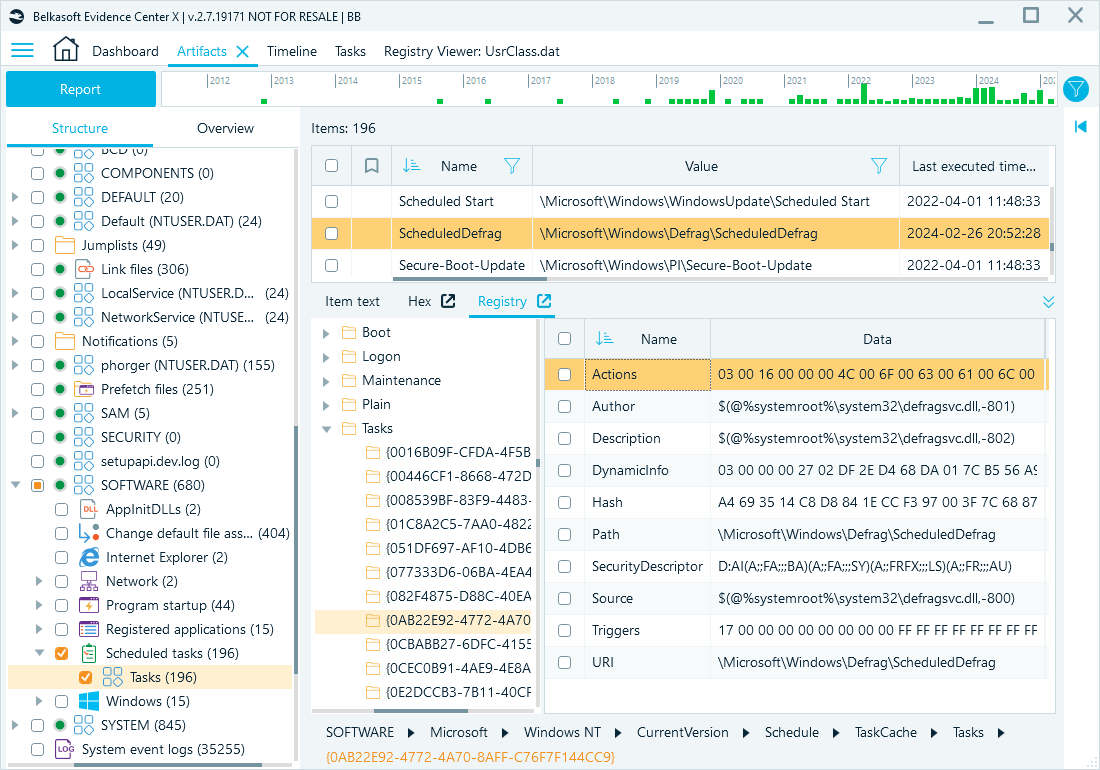
Scheduled tasks in Belkasoft X
Recently accessed documents
Stored in the NTUSER.DAT hive, RecentDocs records include file names and MRU (Most Recently Used) lists, letting you reconstruct part of user activity chronologically.
Registry path: HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs
Belkasoft X artifact tree: System files → <username> (NTUSER.DAT) → Windows Explorer → Recently accessed documents
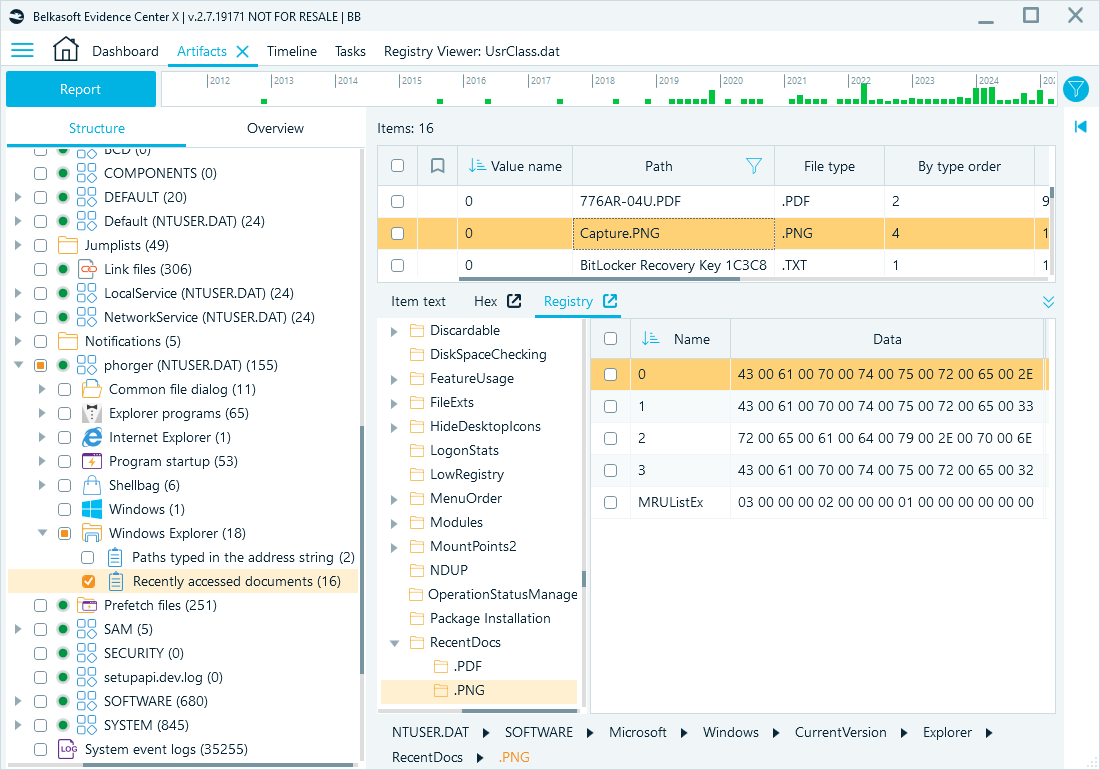
Recently accessed documents in Belkasoft X.
Shellbags
Shellbag data in the NTUSER.DAT hive tracks user navigation and folder view preferences, providing context about user interactions with the file system.
Registry paths:
- HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\BagMRU
- HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags
Belkasoft X artifact tree path: System files → <username> (NTUSER.DAT) → Shellbag → Shellbag
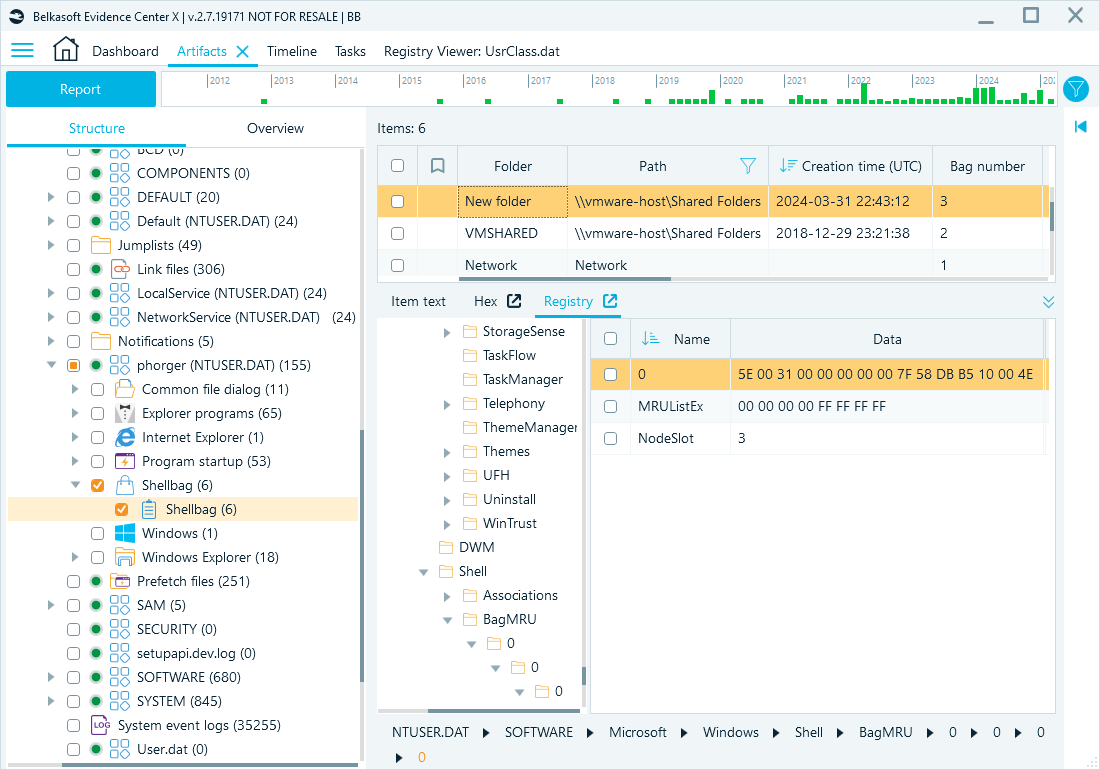
Shellbag records in Belkasoft X
Application usage: Amcache and Shimcache
The Amcache and Shimcache keys store execution artifacts that can reveal historical program usage and persistence mechanisms.
Registry path: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\AppCompatCache
Amcache records provide details of executable programs run on the system, including execution timestamps, file paths, hashes, and sometimes digital signatures. This information can be helpful in reconstructing application execution history.
Belkasoft X artifact tree path: System files → Amcache.hve → Amcache → Amcache
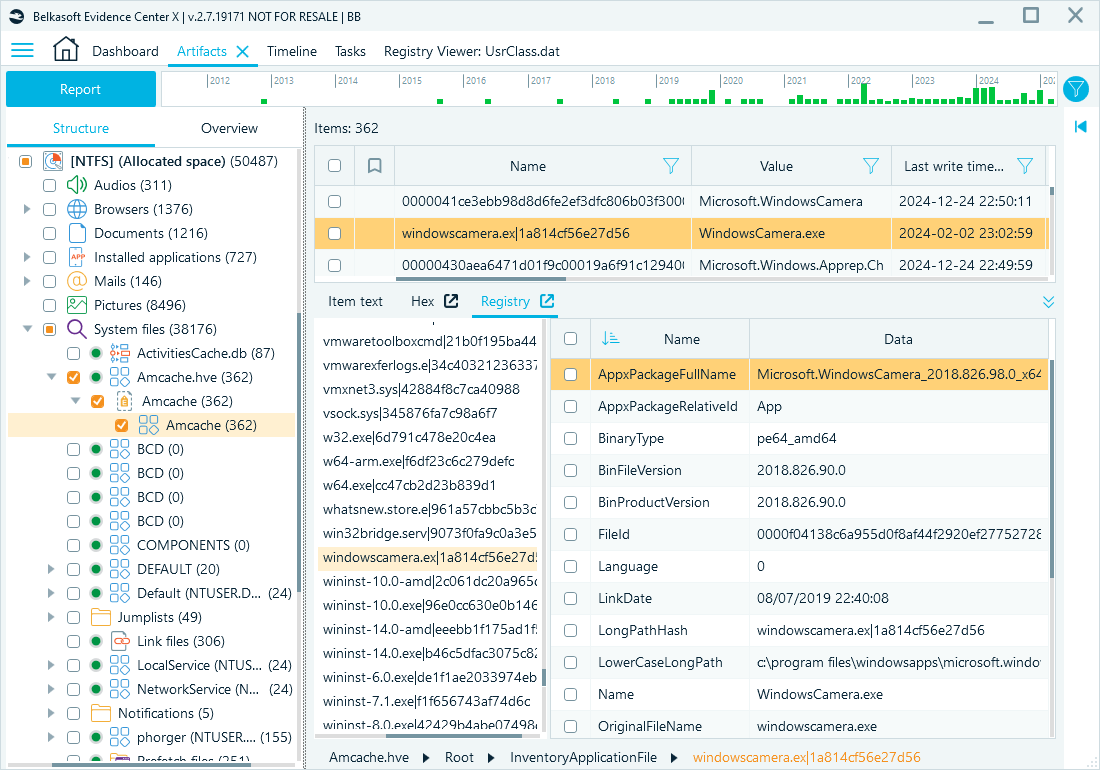
Amcache artifacts in Belkasoft X
Registry path: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\ession Manager\Amcache.hve
Shimcache entries track executables run on the system, even if deleted afterward. Entries often include file paths and timestamps of the last modification or execution, making Shimcache highly valuable for forensic timeline reconstruction.
Belkasoft X artifact tree path: System files → SYSTEM → Application shimming → Recent activity
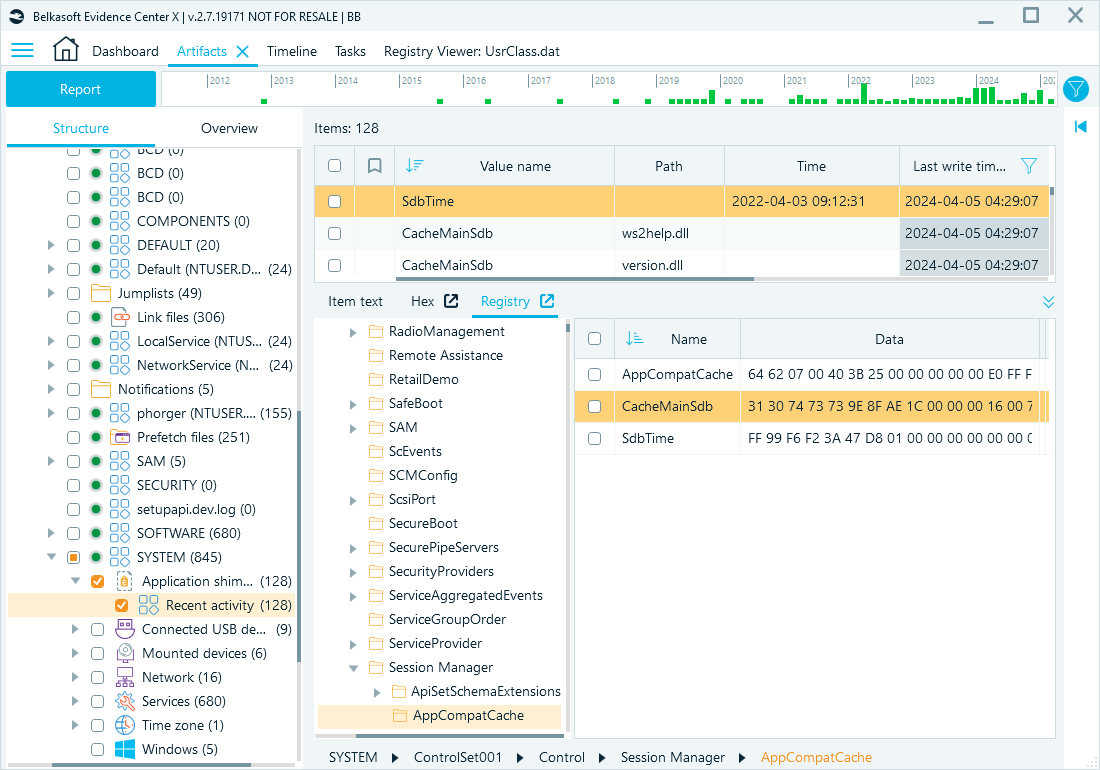
Reviewing Shimcache records with Belkasoft X
Conclusion
The Windows registry can provide insights into user activities, connected devices, software executions, and system configurations. While native Windows tools (RegEdit, PowerShell) provide live access at the risk of altering evidence integrity, registry analysis with Belkasoft X ensures evidence integrity and helps quickly find relevant data. You can explore extracted records in the Artifacts window and dig further into the clues by inspecting the hives in the Registry Viewer.
By selecting the right approach and utilizing registry artifacts strategically, you can effectively reconstruct events, uncover anomalies, and substantiate forensic findings.

