Windows Browser Forensics with Belkasoft X
Web browsers generate a wide range of artifacts, such as log files, cache data, and cookies, as they process user activity, from entering a URL to establishing a network connection. Users may also interact with forms, enter personal information, save passwords, or store credit card details, which browsers often retain for convenience.
This guide explores major browser types, common artifact locations, and critical challenges in web browser forensics, demonstrating how Belkasoft X can streamline digital forensic analysis:
- Major browser types and their data locations
- Chromium-based browsers
- Challenges in browser forensics
- Where to look for browser artifacts
- Chrome browser forensics: Data of interest
- Reviewing Chrome artifacts with Belkasoft X
- Encrypted data in Chrome
- Private browsing artifacts
Read on to learn how to locate, extract, and analyze browser artifacts effectively with Belkasoft X.
Major browser types and their data locations
The specific location of browser data can vary depending on the operating system, browser version, and user settings. However, on Windows systems, most browsers typically store their data in either the %AppData% or %LocalAppData% folders.
Standard PATH values are:
- %AppData% = C:\Users\<Username>\AppData\Roaming
- %LocalAppData% = C:\Users\<Username>\AppData\Local
Folders in the main browser directory for multiple browser profiles—for example, Default, Profile 1, Profile 2—represent individual profiles.
Chromium-based browsers
This category encompasses some of the most popular browsers, including Google Chrome, Microsoft Edge, Opera, and QQ Browser. These browsers share a common foundation—the Chromium engine. The forensic analysis of such browsers can be approached similarly, as they often keep data in comparable formats and directories.
Chromium-based browsers commonly store their data in the %LocalAppData% folder—for example, Chrome's main directory: C:\Users\<Username>\AppData\Roaming.
Gecko-based browsers
Mozilla Firefox, Waterfox, and Pale Moon are prominent examples of Gecko-based browsers. Renowned for their strong emphasis on user privacy, customization, and open-source development, these browsers provide a robust developer console, advanced privacy settings, and a wide range of extensions.
Most Gecko-based browsers use the %AppData% folder for their data. Thus, Firefox's main path will be %AppData%\Mozilla\Firefox\Profiles.
Tor Browser, also built upon the Gecko platform, stores data in its installation folder.
Legacy browsers
The term "legacy browsers" refers to older browsers built on outdated engines such as Trident, EdgeHTML, Presto, KHTML, and others. Internet Explorer and older versions of Microsoft Edge are prime examples. While these browsers may still be used in specific enterprise environments to be compatible with legacy web applications or for nostalgic sentiments, they generally lack support for modern web standards and security features.
Challenges in browser forensics
Summarizing all the above, you can outline the main challenges in browser forensics:
- Data complexity: Browser artifacts are scattered across various formats (SQLite, JSON, proprietary) and locations.
- Encryption: Sensitive information like passwords and credit card details often requires decryption for access.
- Privacy modes: Incognito and private browsing modes leave minimal traces, reducing available artifacts.
On top of these challenges, the increasing reliance on cloud-based data complicates local artifact recovery. Investigators may need access to the cloud environment to retrieve this data, requiring authorization credentials or legal permissions.
Where to look for browser artifacts
You can find browser artifacts in several Windows system locations:
- Local storages typically contain main browser data, such as history, cache, and cookies.
- Memory dumps may reveal active browsing sessions, open tabs, and other volatile data not stored on the drive.
- Hibernation and page files may contain data such as open tabs or active browsing history just before the system entered sleep or hibernation mode.
The latter two are especially valuable for pinpointing webmail traces and capturing private browsing artifacts. To learn about real-world scenarios for using memory dumps to determine the initial attack vector, read the Hunting for Initial Infection Vector with Belkasoft whitepaper.
Chrome browser forensics: Data of interest
While specific locations may vary by browser, operating system, and user settings, Chromium browsers work similarly when it comes to data storage and artifact generation.
Google Chrome allows users to create multiple profiles, each with its own set of data, such as browsing history, bookmarks, passwords, cookies, and sync settings. Profiles are stored as separate folders within the browser's data directory. The Default profile is the primary profile automatically created during Chrome's installation. If additional profiles are set up (for example, when a user has different accounts for work and personal tasks), they are named Profile 1, Profile 2, and so on. This structure enables investigators to isolate account-specific browser activity during forensic analysis.
As we focus on Belkasoft X capabilities, we will look at Chrome's Default profile in this article.
Chrome stores its data in several formats:
| Data | Location | Description |
| Bookmarks | Default\Bookmarks | A JSON file containing saved bookmarks |
| Browser Preferences and Site Preferences | Default\Preferences | A JSON file storing browser and site configuration settings |
| Browsing History and Favicons | Default\Favicons | An SQLite database storing visited URLs and associated website icons (favicons) in the favicon_bitmaps and icon_mapping tables |
| Browsing History | Default\History | Stored in the History SQLite database, in the urls and visits tables |
| Search Queries | Default\History | Stored in the History SQLite database, in the urls and keyword_search_terms tables |
| Top Visited Sites | Default\Top Sites | Stored in the Top Sites SQLite database within the top_sites table |
| Downloads | Default\History | Stored in the History SQLite database in the downloads table |
| Sessions | Default\Sessions | Contains Session and Tabs files for browser session management |
| Cookies | Default\Network\Cookies | An SQLite database storing cookie data |
| Cache | Default\Cache | Includes an index file ('index'), multiple data block files ('data_#'), and individual cached data files ('f_######') |
| Form Data | Default\Web Data | An SQLite database. Includes autofill and related tables, partly encrypted |
| Login Data | Default\Login Data | An SQLite database storing saved credentials |
When examining files containing Chrome data, remember that they include timestamps formatted as a 64-bit value, representing the number of microseconds elapsed since January 1, 1601, at 00:00 UTC.
Reviewing Chrome artifacts with Belkasoft X
While you can explore Chrome data using various viewers, working with encrypted information and finding connections between records will require a digital forensics tool.
Belkasoft X parses, collates, categorizes, and indexes browser artifacts, making them searchable:
Reviewing browser artifacts in Belkasoft X
This section will review Chrome artifacts and highlight their unique details.
Bookmarks
Chrome bookmarks are stored in the Default folder, the Bookmarks JSON file:
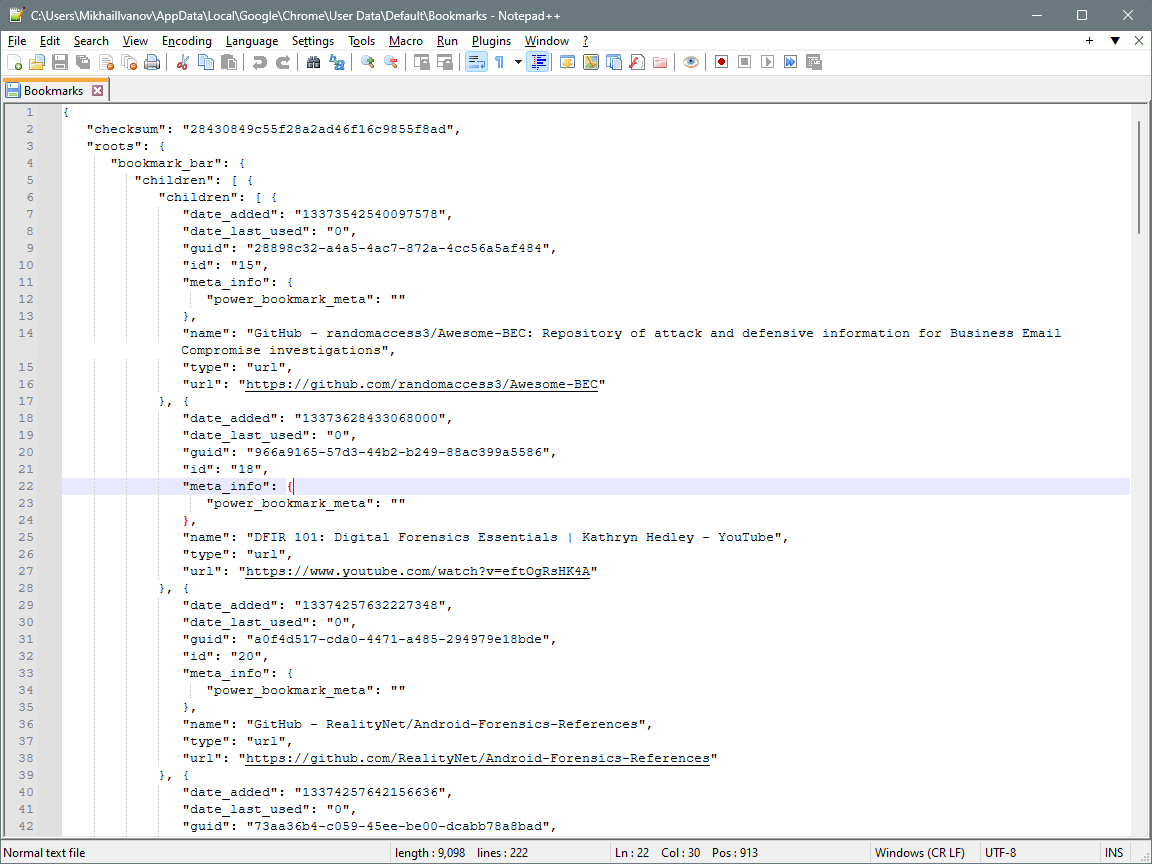
JSON-formatted Google Chrome bookmarks
Belkasoft X parses bookmark details and places them under the Favorites subnode of each browser profile:
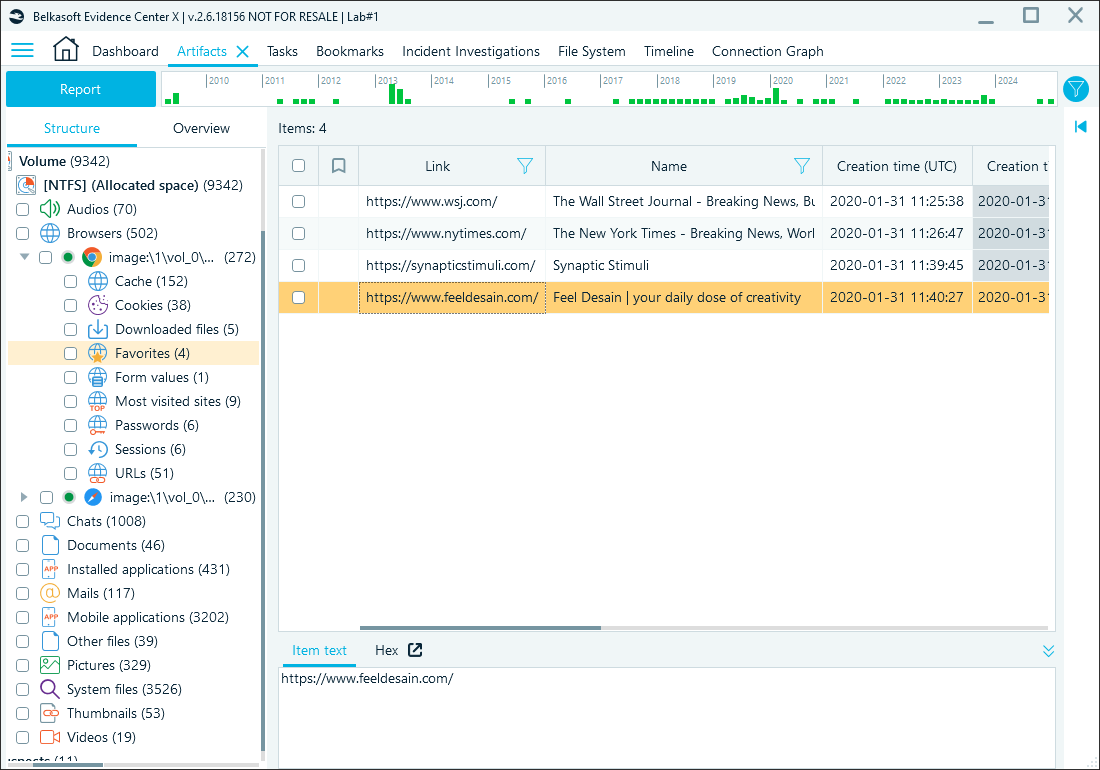
Google Chrome bookmarks in Belkasoft X
Browsing History
Browsing history analysis helps uncover a user's online activities, including visited websites, search queries, location lookups, download records, and the associated timestamps. It can help establish timelines, identify intent, and find potential evidence of illicit activity or communication relevant to an investigation. Most of this valuable information is part of the History SQLite database.
Another database worth exploring for browsing history reconstruction is the Favicons database. Although its primary purpose is to store website favicons for faster tab loading, it can also be valuable in digital forensics. This database contains not only URLs of visited pages but also timestamps for part of those visits, and in some instances, it may retain URLs that have been purged or deleted from the History database.
Belkasoft X parses browsing details from both of these databases and shows them under the URLs profile:
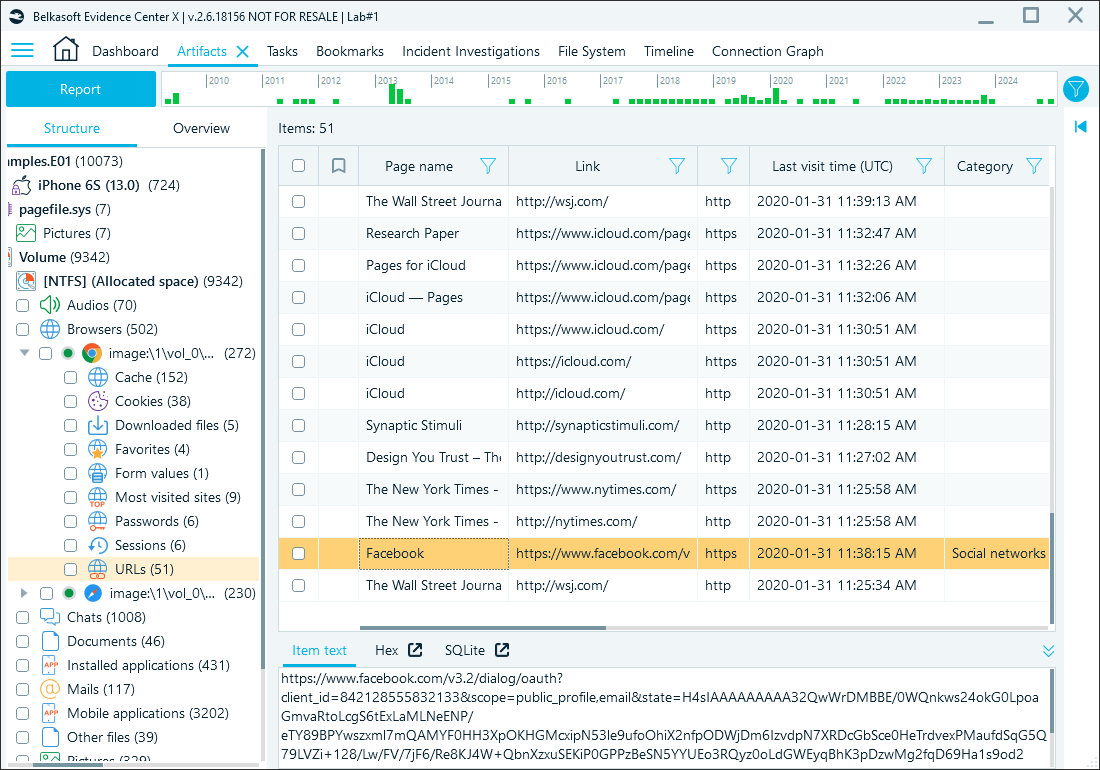
URLs node in Belkasoft X
To reconstruct browser history manually, you must correlate visits and urls tables from the History database by the id field. Similarly, you must match the favicon_bitmaps and icon_mapping tables by the id column to review all URL records in Favicons.
You may find purged or deleted URLs by exploring these databases in Belkasoft X's SQLite viewer. Because of the way SQLite writes records to database pages, fragments of purged or deleted data may remain in the unallocated space. Belkasoft X carves URLs from these fragments and displays them in the Unallocated space section of the SQLite viewer. You can export these findings as a CSV file and search for specific websites or keywords.
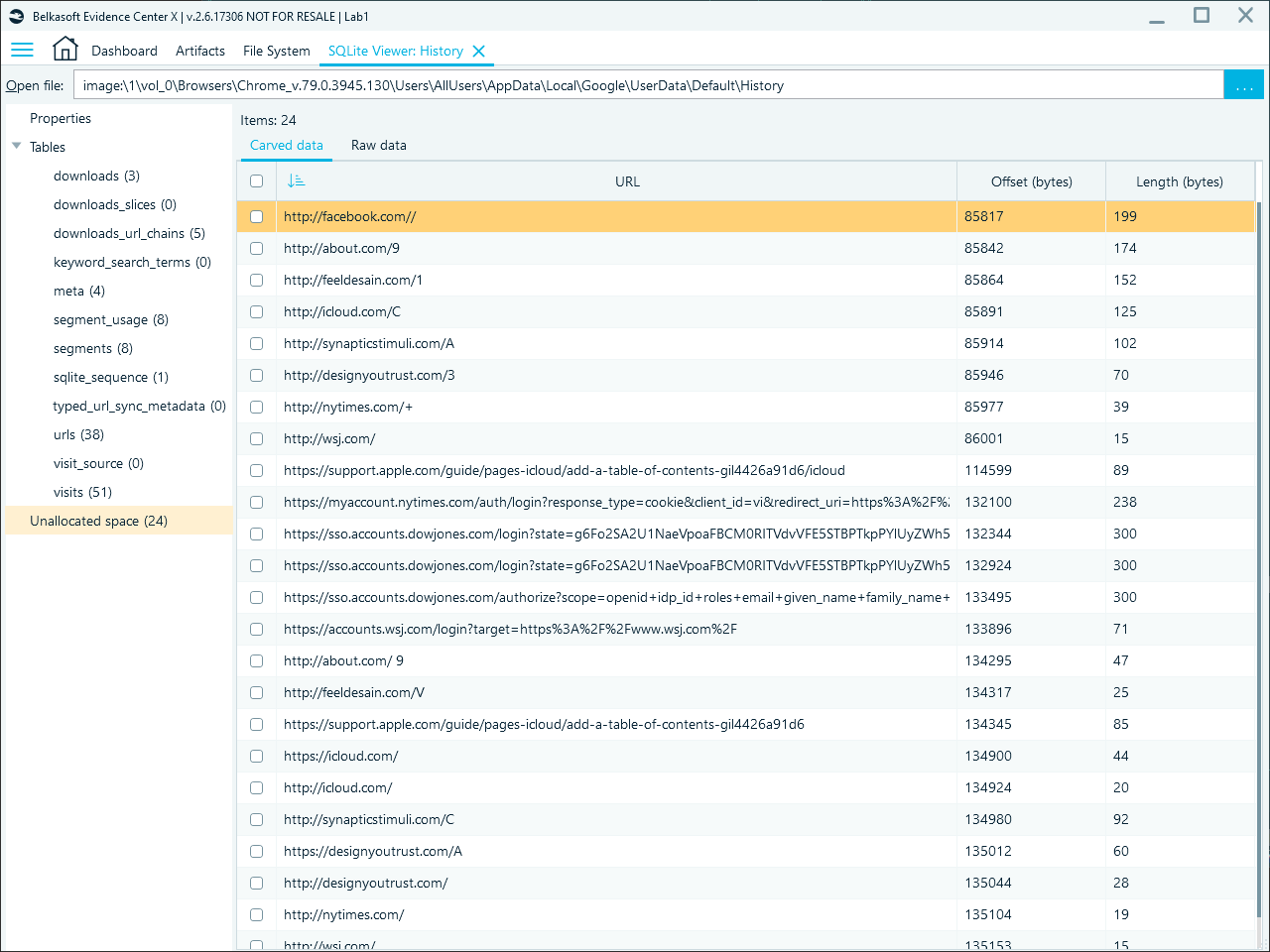
URLs carved by Belkasoft X from unallocated space in the History database
Search queries
Chrome logs search queries separately from general URLs and store them in the urls and keyword_search_terms tables of the History database. Belkasoft X extracts these entries and shows them in the Search term column along with the timestamps of when they were entered:
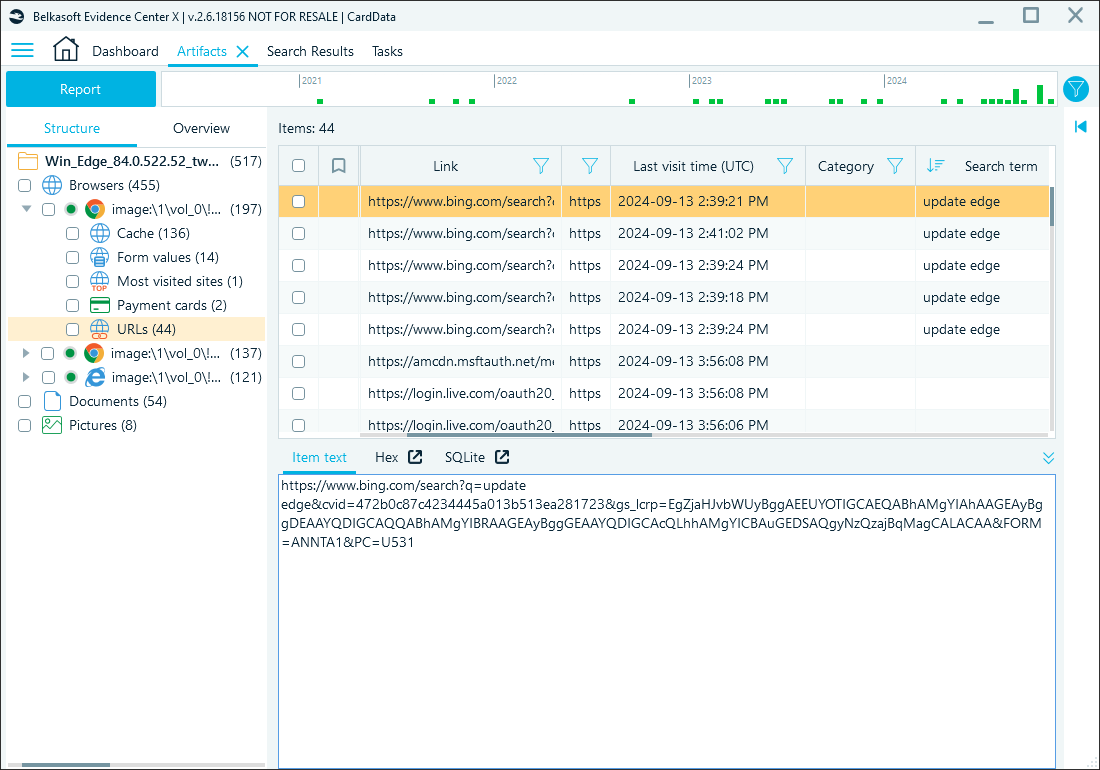
Search terms in Belkasoft X
You can also discover all search queries available in your data source by running the Search engine results automatic search from the main dashboard:
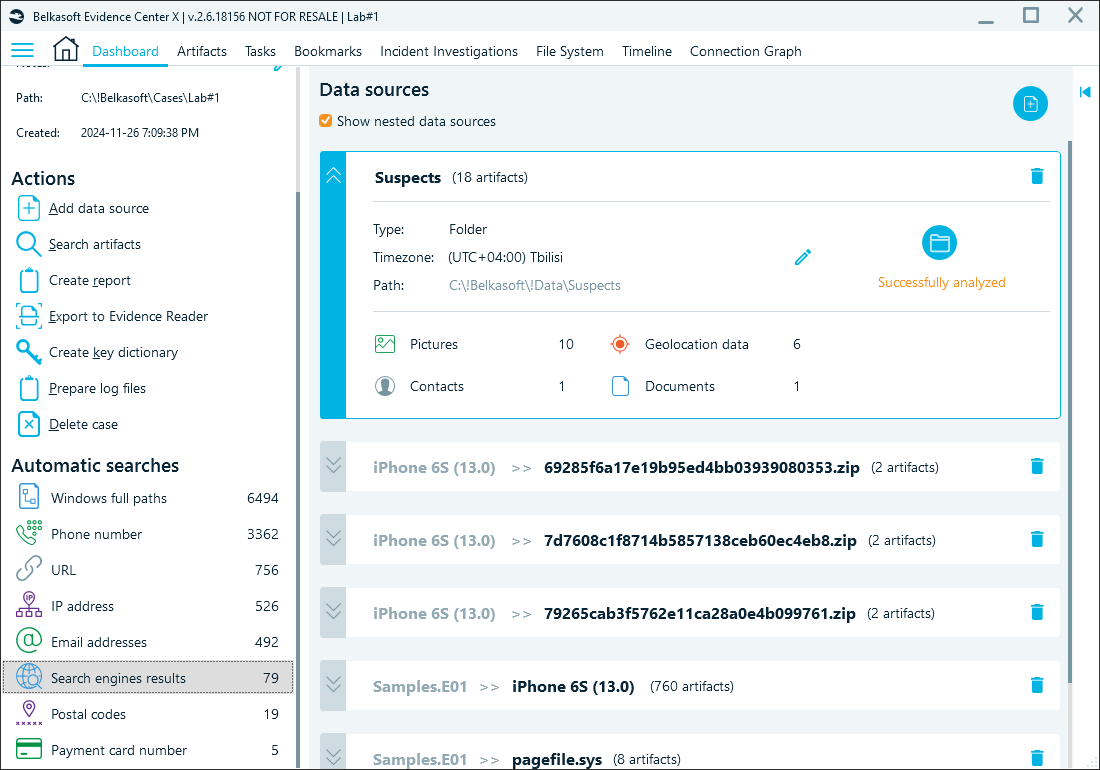
Automatic searches in Belkasoft X's dashboard
Top visited sites
Another valuable artifact in Chrome forensics is the list of top visited sites stored in the Top Sites SQLite database within the top_sites table. Belkasoft X parses this data and displays it along with associated details under the Most visited sites profile:
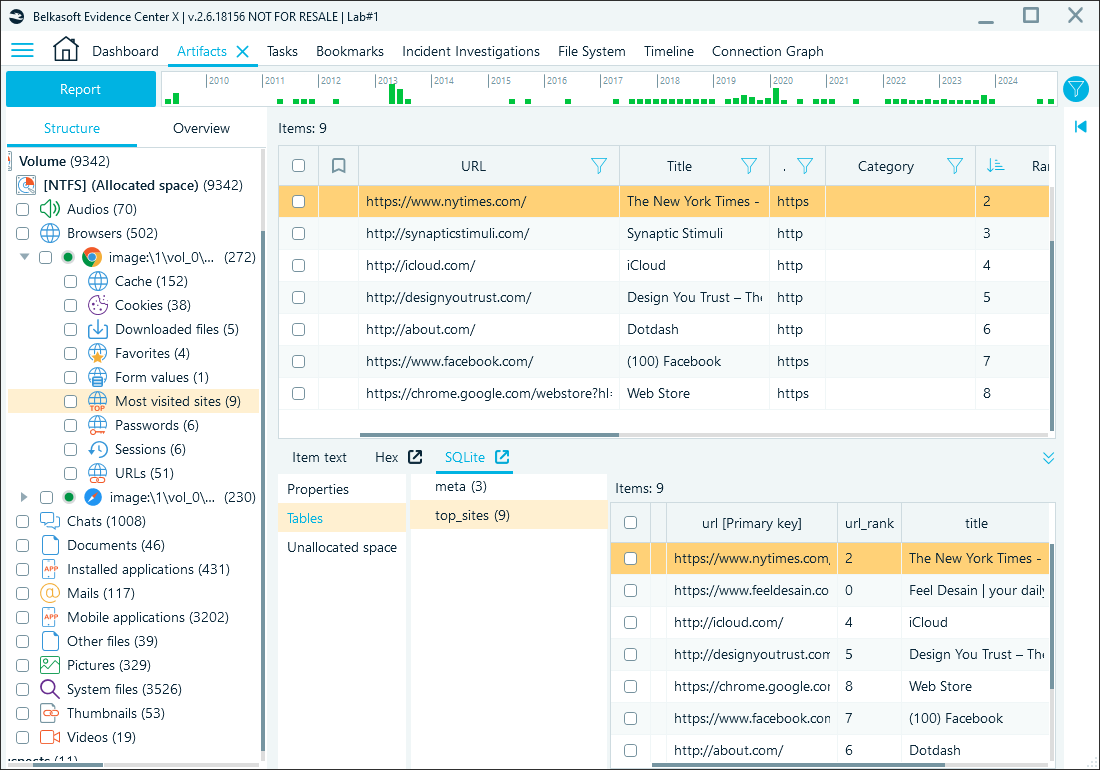
Reviewing Visits table in Belkasoft X's SQLite viewer
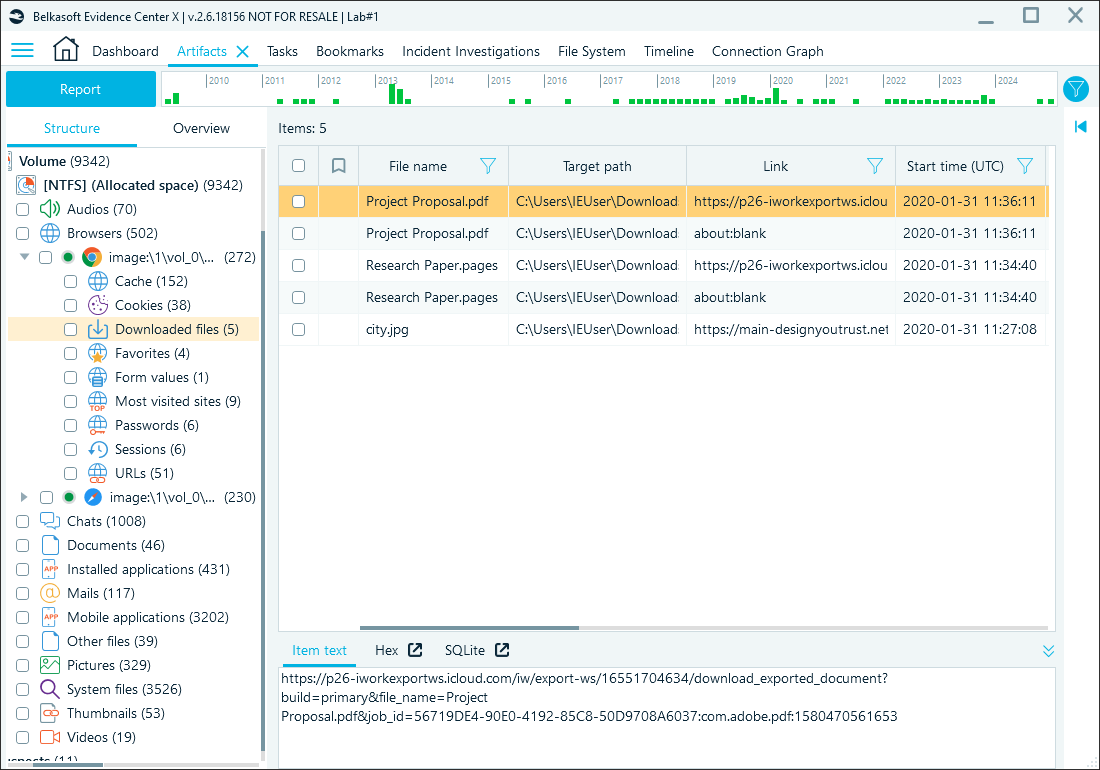
Downloads
Chrome records the details of the downloaded files in the History database's downloads table. Belkasoft X simplifies access to this data by displaying it in the Downloaded files node:
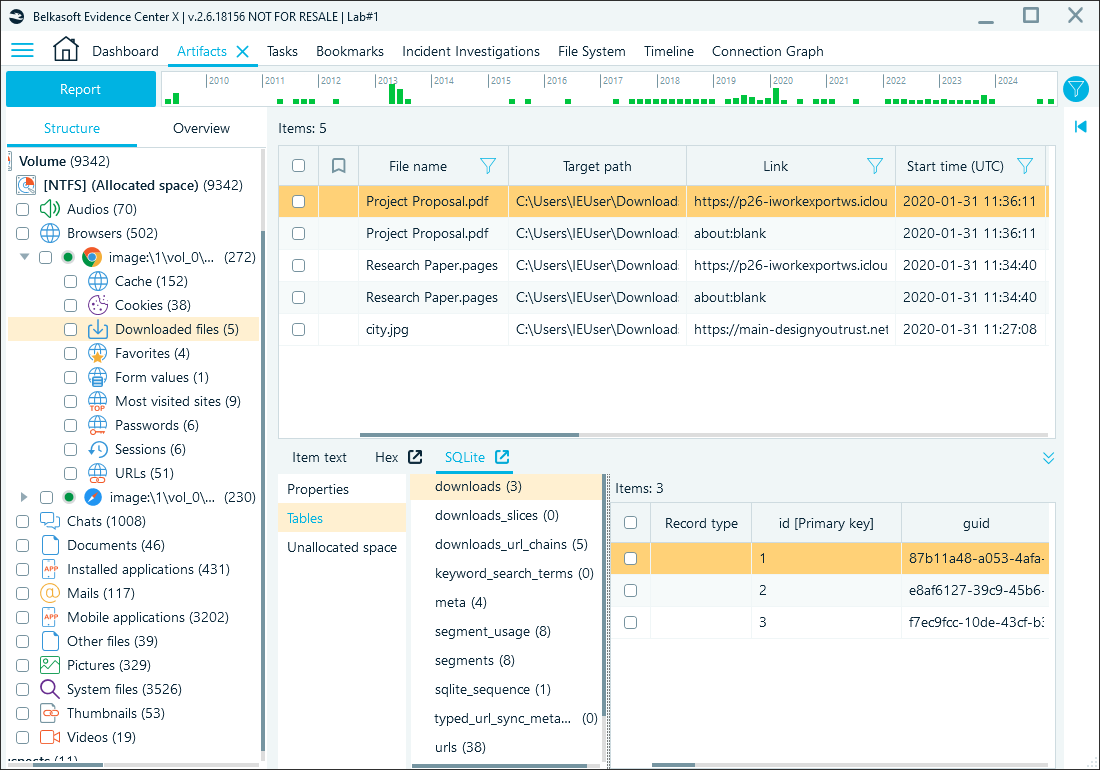
Download records in Belkasoft X
The downloads_url_chains table captures the URL redirection chain for downloaded files. It can help you uncover potential malicious or unexpected sources of downloaded files.
Sessions
Stored in the Default\Sessions folder, session remnants can reveal ongoing user activity—if a device is acquired mid-session—or provide evidence of recent activity even after the user has logged out. These remnants may include open tabs, session tokens, or partially completed actions, depending on the timing and method of data acquisition.
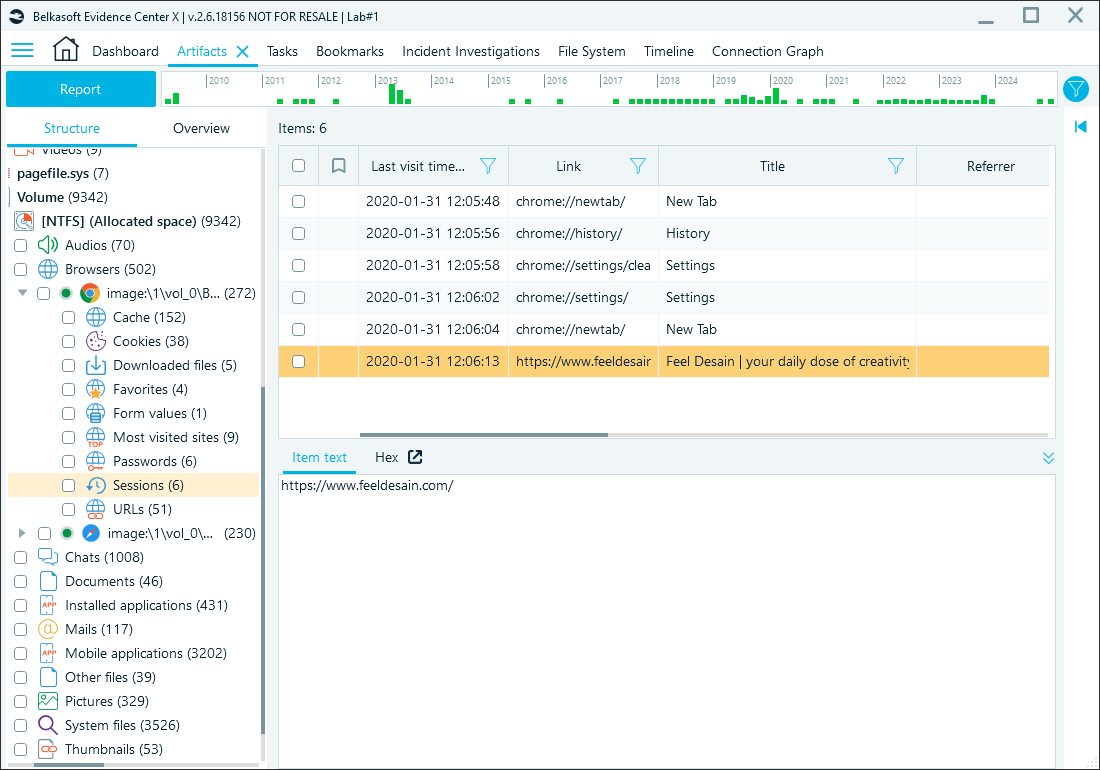
Browsing sessions in Belkasoft X
Cookies
Stored in the Default\Network folder, cookies can confirm logged-in sessions, track interactions with specific services, or show evidence of targeted tracking or advertising. Chrome keeps them in the SQLite-based Cookies database. Belkasoft X displays cookies in the dedicated node:
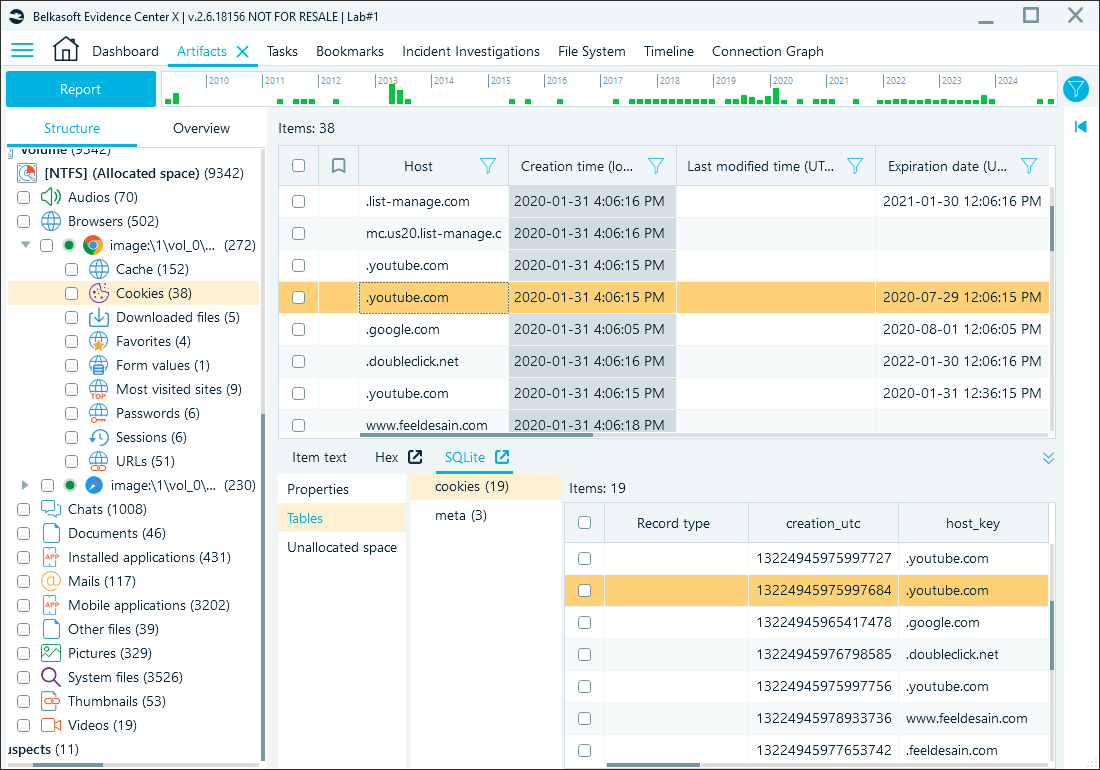
Cookies review in Belkasoft X
Form autofill data
Located in the Default folder, the Web Data database includes autofill entries such as names, addresses, phone numbers, and email addresses that users input into web forms. This data can provide additional information on the user and their online activities. In Belkasoft X, you can locate it under the Form values profile:
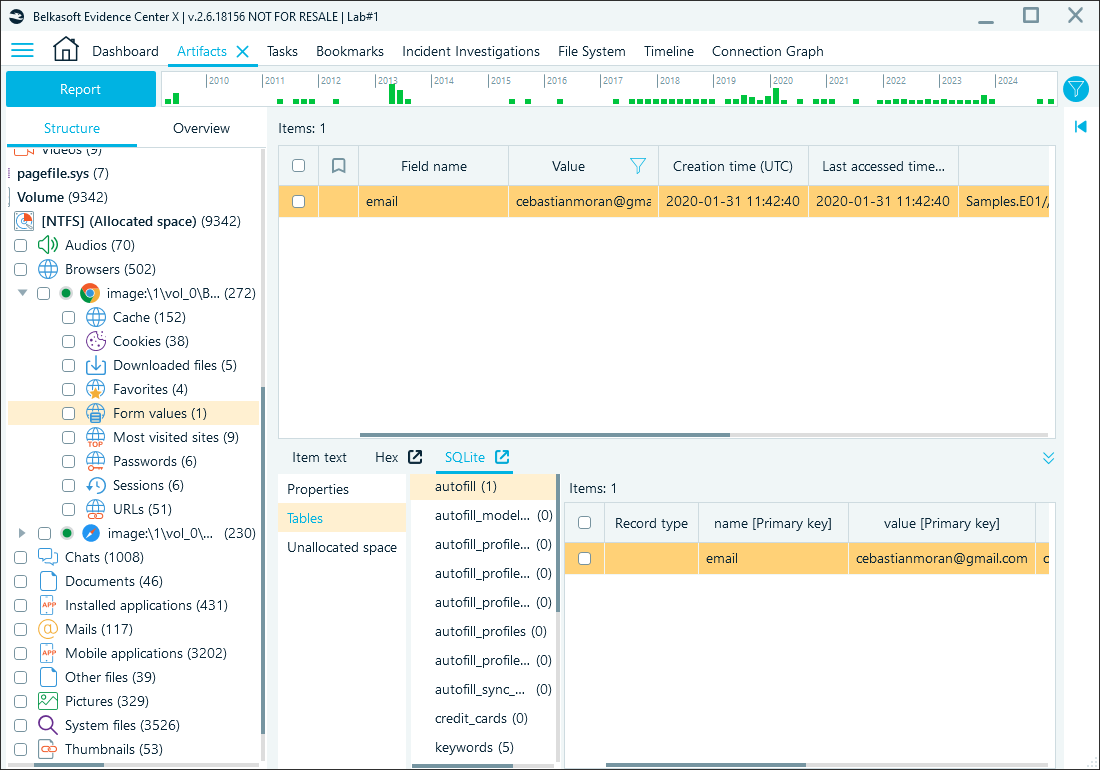
Form autofill records in Belkasoft X
Cached files
Cached items in the Default\Cache folder include transient data like images or scripts from visited sites. Chrome stores cached data using three types of files:
- Index File (with filenames like 'index'): This file acts as a directory or map for the cache. It keeps track of all cached items, including their identifiers, storage locations, and metadata. The index file provides the structure necessary to locate data within the other cache files, but does not store the actual content.
- Data Block Files (usually named 'data_#' with the # character as a wildcard) contain cached data in chunks or blocks. They often store multiple items that can be compressed or fragmented. Data Block files are critical for reconstructing content but can be challenging to analyze manually due to their non-standard format and lack of extensions.
- Separate Data Files (with file names formatted like 'f_######'— also with the hash symbol as a wildcard): These are standalone files for individual cached items, such as images, HTML files, or scripts. Unlike data stored in Data Block files, these files are not fragmented but lack extensions, making it unclear what type of data they contain without analysis.
Belkasoft X extracts both types of cache—individual cache files and multi-file data blocks—giving you direct access to cached content. This functionality enables quick previews and analysis of cached artifacts, eliminating the need for additional tools or tedious manual guesswork.
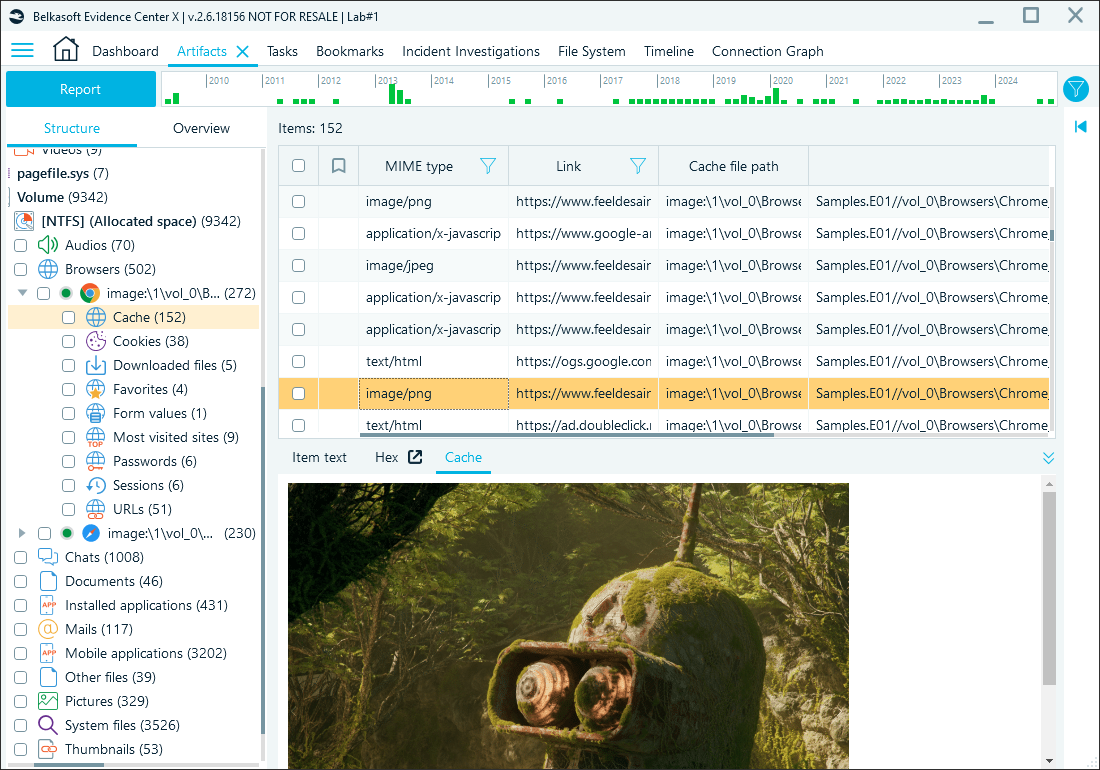
Reviewing browser cache in Belkasoft X
Encrypted data in Chrome
Similarly to most popular browsers, Chrome can store autofill data, including passwords and credit card information, for the user's convenience. Confidential data is encrypted on Windows computers with the CryptProtectData function, which requires OS-level decryption.
When analyzing Chrome data, Belkasoft X detects encrypted information and prompts you to provide the credentials to decrypt it in the Tasks window. Here, you need to enter the user's Windows system password and the path to the files in the user's Protect folder:
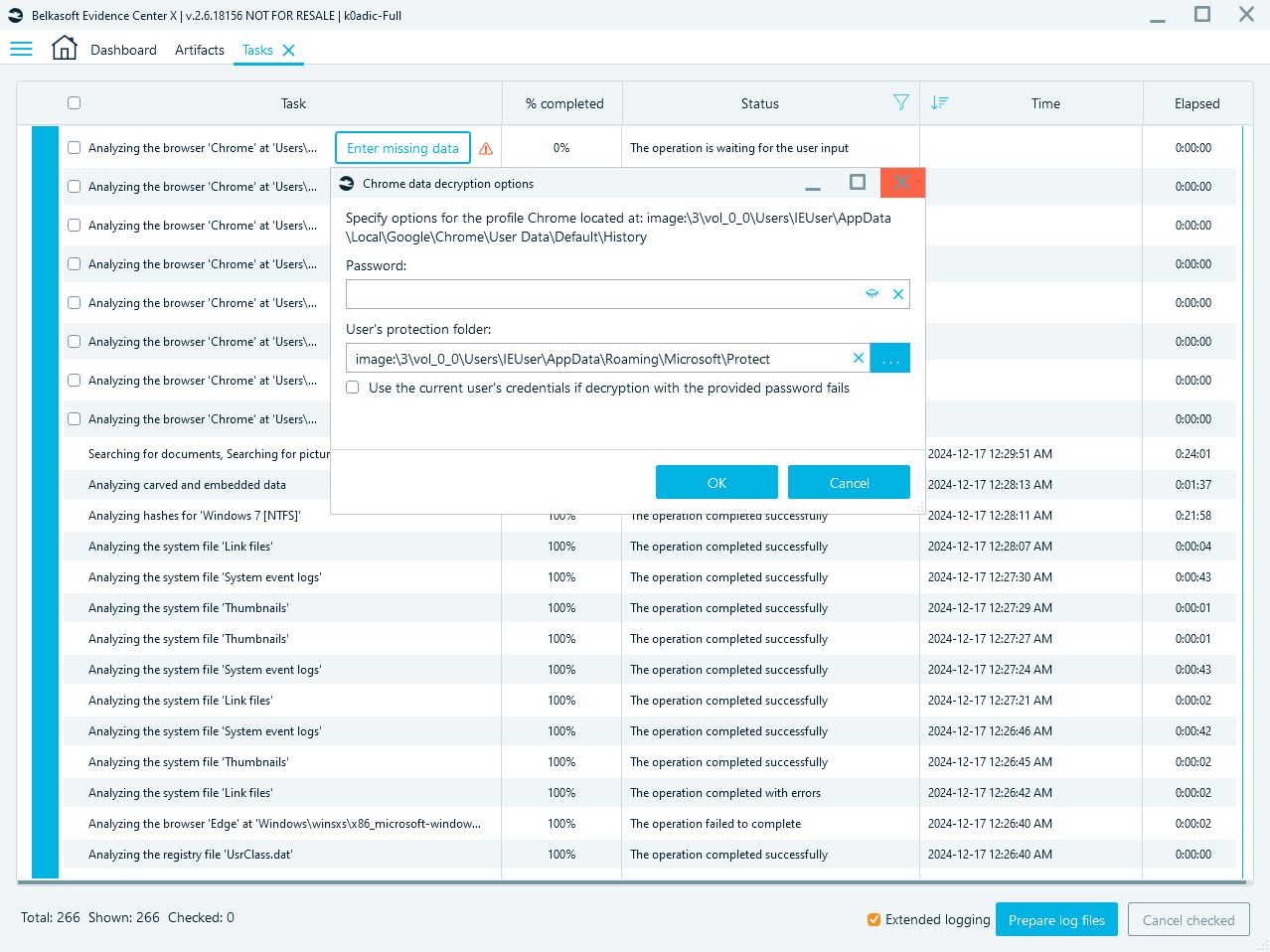
Chrome decryption dialog in Belkasoft X
Passwords
Passwords are stored in the Default folder, Login Data SQLite database. Password values become available in plain text after being decrypted by Belkasoft X. These credentials provide direct access to user accounts, shedding light on other linked data sources and user activity:
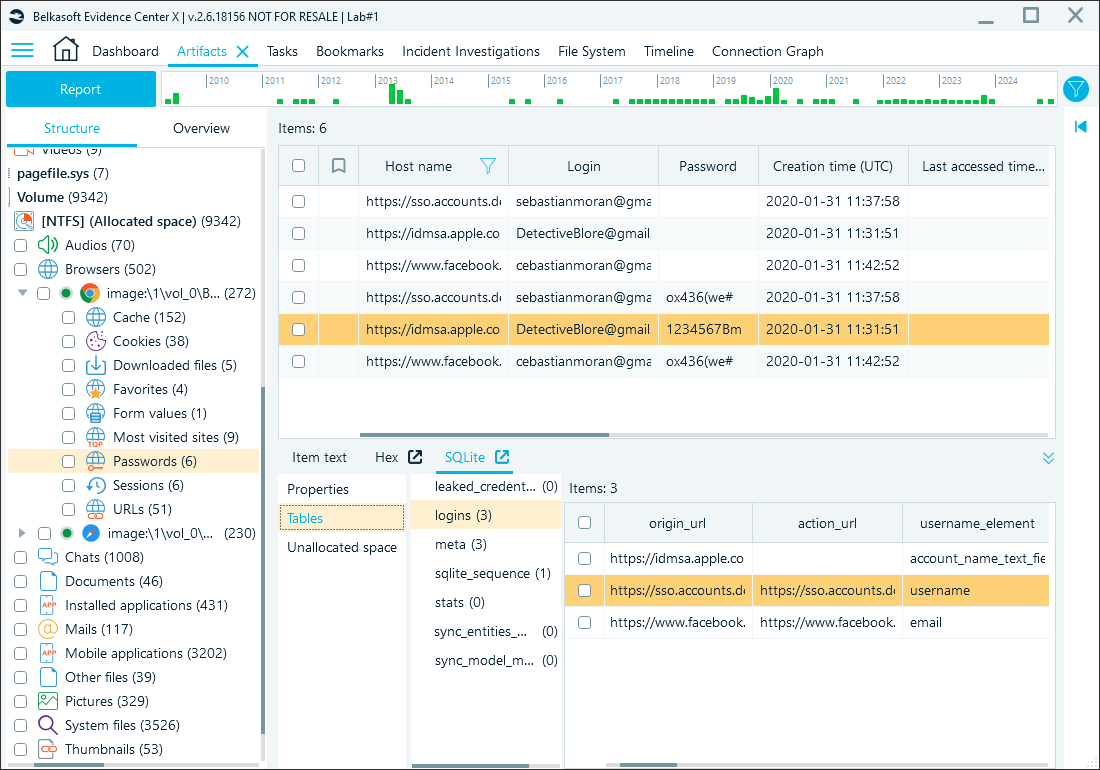
Decrypted Chrome password data in Belkasoft X
Credit card information
Beyond standard form data, Chrome's Web Data database can also retain saved credit card details, including cardholder names, card numbers, expiration dates, and billing addresses. Belkasoft X displays this information under the Payment cards profile. Card numbers are stored in an encrypted form and, when successfully decrypted, are shown in the dedicated column:
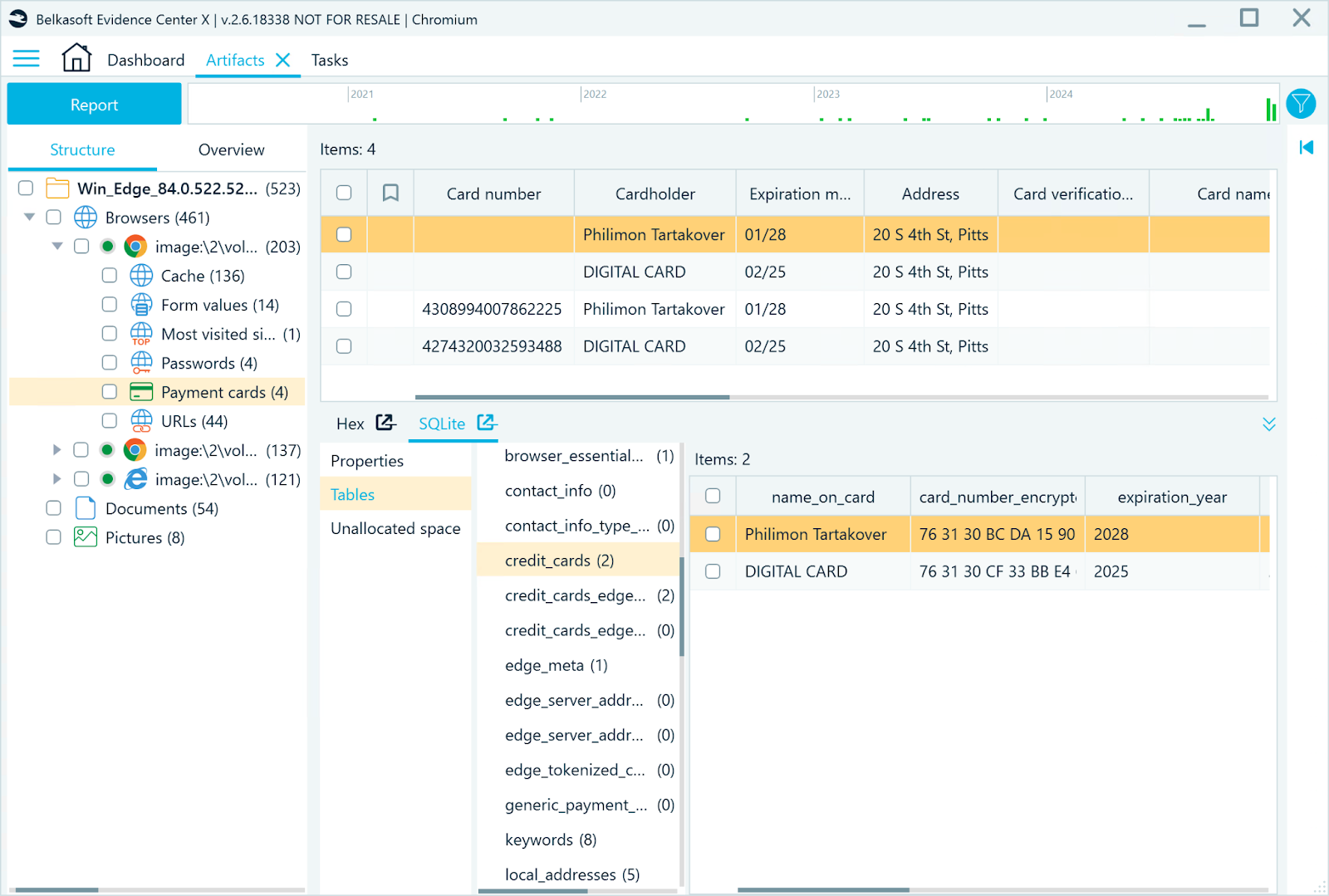
Credit card data with decrypted card numbers in Belkasoft X
Private browsing artifacts
Secure browsers, such as the aforementioned Tor browser, and incognito (or private) browsing modes of some browsers are designed to limit local data storage during a browsing session. However, they still fall short of offering total anonymity, as some artifacts are still retrievable from:
- Memory: System memory often holds active session data, including incognito activity, but this data is volatile and requires immediate capture before the session ends.
- Pagefile and Hibernation Files: Operating system files like pagefile and hibernation files may inadvertently store fragments of incognito session data, such as open tabs or URLs.
- Unallocated Disk Space: Residual data from incognito sessions might persist in unallocated or slack space.
- Browser Extension and Plugin Data: Certain extensions or plugins may not fully adhere to incognito mode's privacy settings and may log data from private sessions.
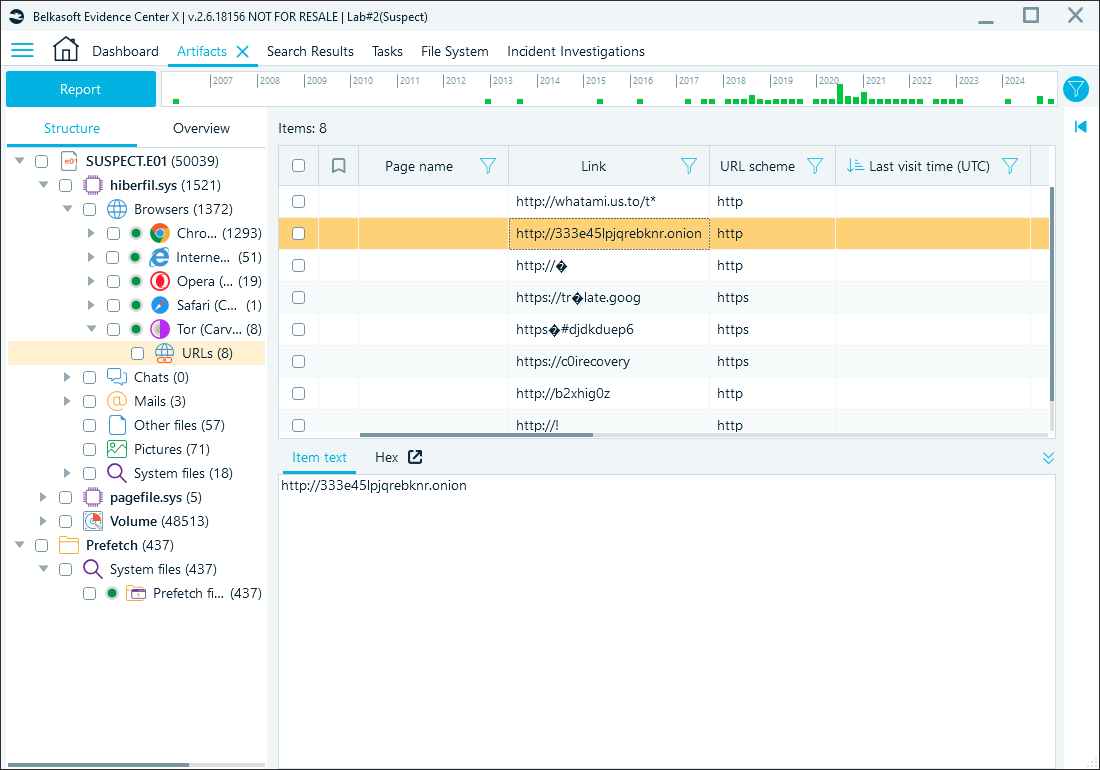
Reviewing Tor browser artifacts found in a hibernation file with Belkasoft X
While private browsing enhances user privacy, it is not foolproof. Due to the volatile nature of these artifacts, analysis timing is crucial.
Conclusion
Web browsers generate an extensive range of artifacts, which makes them a goldmine of evidence for investigations. From bookmarks and search queries to cached files and encrypted credentials, these artifacts can help reconstruct user actions, identify intent, and uncover hidden connections.
Belkasoft X simplifies the tedious task of extracting and analyzing browser data: with features like automatic decryption, integrated previews, and structured categorization, you can efficiently navigate browser artifacts without manual parsing. As browsers and their privacy features continue to evolve, tools like Belkasoft X are essential for staying ahead in digital forensics.
