Mobile forensics is a moving target. In our recent article, “The Future of Mobile Forensics”, we described acquisition techniques that used to be state-of-the art back then. Weeks later, some things have changed already. Three months after the publication a lot of things have changed. Our publication was published on Forensic Focus and discussed in online forums, with readers pointing to certain inaccuracies in our article. In this follow-up, we will use up-to-date information to address the issues of concern in the original article.
iOS 8.4 Forensics
Little changed in iOS 8.x forensics since publishing our original article. Some advances have been made though. iOS 8.4 was successfully jailbroken by the TaiG team (http://www.taig.com/en/), and physical acquisition is once again available for jailbroken 32-bit iOS devices. However, 64-bit Apple hardware (including iPad mini Retina, iPhone 5s and all newer models) successfully resists physical acquisition attempts. Full-disk encryption still rules out chip-off, and there were never JTAG ports in Apple hardware. Unallocated space is still not recoverable as iOS does not keep decryption keys for unallocated areas.
One of our readers drew our attention to an acquisition method often referred as “Advanced Logical”. Besides physical acquisition, this was the only method allowing to extract mail. As far as we know, Apple shut the door to advanced logical acquisition in iOS 8.3, so only older devices remain susceptible to this method. Since Apple does not publish detailed iOS version breakdown (counting iOS 8 in general without giving any insight on how many users switched to the latest release), we do not know what percentage of devices running iOS 8 is still susceptible to advanced logical acquisition.
Apple constantly tweaks iCloud security, making adjustments to lifespan of binary authentication tokens that can be used by experts instead of the user’s login and password (and bypassing two-factor authentication).
iOS 9 Forensics
The latest version of iOS is a hot topic in the world of mobile forensics. With as many as 61% of eligible iOS devices running the latest version of the OS by the 19th of October 2015, iOS 9 is a major concern to forensic crowd.
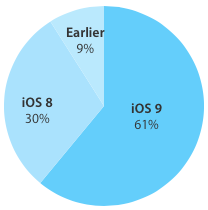
The share of Apple devices running iOS 9 reaches 61% and growing [source]
Featuring so-called “rootless” security system, the new generation of Apple’s mobile OS integrated a number of techniques to constrain security research. While this did not stop the Pangu team from releasing a working jailbreak (http://www.downloadpangu.org/pangu-9-download.html), the existence of this exploit change little in the way of acquisition. So let’s recoup which acquisition options are available for iOS 9 devices:
Physical acquisition
For devices running iOS 9, physical acquisition remains a limited theoretical possibility. While 64-bit devices (iPhone 5S and newer, iPad mini 2 and newer) are out of the question, even 32-bit devices running iOS 9 remain resistant to existing methods of physical acquisition – even if they are unlocked and jailbroken. As such, no existing forensic tools can do physical acquisition of *any* iOS 9 device regardless of jailbreak status and architecture.
Status: physical acquisition is currently unavailable for all iOS 9 devices. This may change in the future, as physical acquisition of 32-bit devices remains a theoretical possibility.
Advanced logical acquisition
Nope. Advanced logical acquisition does not work on iOS 9 devices. And, unfortunately for us all, it is very unlikely that it is going to work later.
Logical acquisition
Logical acquisition remains available via the usual routine. Apple changed the format and encryption used in iTunes backups, so you will need to update whatever forensic software you are using to the latest version in order to gain iOS 9 support.
Our flagship product Belkasoft Evidence Center supports analysis of iTunes backups of devices running iOS 9. The product finds and analyzes data from several dozens of iOS applications, including both most common and some of the newest apps: Skype, Viber, WhatsApp, Kik, WeChat, Whisper, FireChat, MeetMe, Tinder, ooVoo, MeowChat, and many more:
Over-the-air acquisition
Things get tricky when we speak about cloud acquisition of iOS 9 devices. Apple changed a lot of things in iOS 9 when it comes to cloud backups. There is a new data format, and there is a different type of encryption used. The biggest change, however, is the location of the cloud backup. Previously stored in Apple iCloud, iOS 9 backups are now saved into iCloud Drive, a cloud service with very different internal mechanics.
At this time most of forensic software manufacturers are yet to adjust their products to able to acquire iOS 9 data from iCloud Drive. It is worth noting that binary authentication tokens continue to work in their usual fashion, allowing to bypass two-factor authentication if you happen to use a non-expired token.
Android Forensics
There have been few advances in this area. A recent vulnerability report by Check Point introduces a backdoor allowing experts acquiring some Android devices remotely. One of our readers noted that bootloader-level exploits are available for many Android models and used by Cellebrite in their acquisition tools to dump the content of Android devices without rooting the phone.
Certifi-Gate
A major security vulnerability was discovered in Android by Check Point Software Technologies and revealed at Black Hat in Las Vegas. Dubbed Certifi-Gate, the vulnerability exists on millions of devices such as those manufactured by LG, Samsung, HTC, and ZTE, allowing attackers gain total control over affected devices remotely. The vulnerability exists in remote support tools pre-installed by some manufacturers to Android handsets in order to help users solve problems with their devices remotely. These tools include TeamViewer, MobileSupport (by Rsupport) and CommuniTake Remote Care. Apparently, a vulnerability exists in these tools allowing an attacker to use their security certificate to take over an Android device.
There is no way for the end user to revoke or invalidate the certificates. Waiting for a patch or uninstalling affected tools is the only protection method, and even that may leave behind a vulnerable certificate. Check Point estimates several million devices to be affected by this vulnerability.
At this time, we are not aware of any forensic tool that is able to exploit this vulnerability to gain access to Android devices. We do not know if it is even feasible to exploit this vulnerability to gain such access.
Stagefright and Stagefright 2.0
This famous security vulnerability has potential, yet the possibility of its forensic use for the purpose of gaining access to the phone’s data partition is questionable. So far, no forensic solutions that use this exploit exist.
Bootloader Exploit
Most Android devices sold by reputable vendors (including Samsung, LG, SONY, HTC, ASUS and many others) feature permanently locked bootloaders to protect devices against booting unsigned code. Physical acquisition options for bootloader-locked devices are limited, especially in latest versions of Android. On many devices, rooting devices even temporarily requires unlocked bootloader as a pre-requisite.
One of our readers pointed out that a bootloader-level exploit exists for many devices, and successfully implemented by Cellebrite in its acquisition kit. Cellebrite UFED can successfully boot some locked devices with an unsigned patched boot image to allow extracting device image.
The exploit exists in many devices based on the Qualcomm reference platform and using Qualcomm reference software. As a result, devices using an affected kernel can be booted with a patched kernel image without proper security verification.
Cellebrite were able to exploit this vulnerability to boot many affected models with their own patched kernels. This is not an easy task since a unique kernel had to be built for each individual device. Several hundred models are reported to be affected by this vulnerability.
If available for a given device, a bootloader attack is arguably the most forensically sound acquisition method available. Since booting an external image does not write anything to the device nor changes any part of the system image, it is able to consistently extract unmodified images of the device that will persistently pass hash checks. Alternative physical acquisition methods work by acquiring root privileges and install acquisition agents onto devices being acquired, which inevitably alters the content of the device.
Bootloader exploits are device specific. Cellebrite claims support for most Motorola Android devices, selected Samsung, Qualcomm, LG GSM and CDMA devices based on Qualcomm chipsets. Caution is required when using bootloader exploits as some devices are known to wipe data partition when booting a custom image.
Custom Recoveries
We have been asked whether a custom recovery such as TWRP or CWM can be used to boot the phone (tethered boot) and pull data partition. While this can be technically possible, particularly on devices with unlocked bootloaders or having a known bootloader exploit, booting a custom (read: unsigned) recovery can (and, in fact, does) trigger the phone’s protection mode, causing the device to wipe the content of the data partition immediately upon booting into recovery and without giving any sort of advance warning. For this reason, we cannot recommend custom recoveries as a viable forensic acquisition method.
Windows Phone 8 Forensics
With Windows 10 Mobile coming soon and considering the small market niche occupied by Windows Phone devices in general, Windows Phone 8 is becoming a white elephant. However, developments are made to Windows Phone acquisition as well. We have the following data to add to our previous publication.
Windows Phone 8/8.1 Encryption Explained
When we mentioned Windows Phone acquisition, we had to talk about JTAG and chip-off acquisition (more on the subject here: https://belkasoft.com/jtag-analysis). Since most Windows Phones are consumer devices, their content is not encrypted, and JTAG works properly. However, we have been contacted by a customer who claimed that they had an encrypted Windows Phone device, and asked for help.
Windows Phone 8/8.1 do not have an option for the end user to control encryption of Windows Phone 8.x smartphones. Instead, encryption can be enabled or disabled by a group policy specified by the administrator of the corporate MDM (Microsoft Mobile Device Manager). If encryption is triggered by an MDM policy, the device will automatically encrypt the content of the user partition with BitLocker. As a result, JTAG and chip-off will not return a decryptable image.
What about BitLocker escrow keys? According to Microsoft, the Windows Phone 8 OS does not come with the provision of maintaining escrow keys outside of the device (unlike desktop versions of Windows featuring downloadable BitLocker Recovery Keys). Since private users cannot manually activate encryption in Windows Phone 8, the usual approach of grabbing escrow keys from https://onedrive.live.com/recoverykey will not work for Windows Phone devices.
So what happens when one is trying to acquire an encrypted Lumia phone with BitLocker encryption enabled through corporate device policies (consumer devices do not)? While one can technically make Windows Phone to ask for a BitLocker recovery key at some stage (e.g. http://www.windowscentral.com/bitlocker-cyan-update-problems-windows-phones), the escrow key itself is never created, saved, or uploaded anywhere.
Windows Phone Bootloader Exploit
As suggested by a reader, an additional acquisition option is available for select Windows Phone devices. Some popular Windows Phone 8 devices such as Nokia Lumia 520 are susceptible to a bootloader exploit that enables physical acquisition of said devices. Cellebrite's UFED is able to perform physical acquisition of select Windows Phones devices. Unencrypted images acquired via this method will contain full raw dumps of the phone’s storage. Supported Windows Phone 8 devices can be dumped with Cellebrite UFED via a USB cord.
Belkasoft Evidence Center fully supports analysis of UFED images. The product will automatically analyze the image, locating and laying out for you its contents: calls and messages, chat and messenger apps, email boxes, payment system apps, and so on.
Simply import the image to Belkasoft Evidence Center, and it will locate dozens
of forensically important artifacts – completely automatically
Windows 8/8.1/10 and BitLocker
We were asked about ways to recover BitLocker escrow keys from the corporate MBAM (Microsoft BitLocker Administration and Monitoring). If a corporate account was used on a certain Windows computer, and the company maintains a MBAM to manage BitLocker keys, the first thing to verify is checking whether the MBAM had a policy of not using escrow keys (https://technet.microsoft.com/en-us/library/dn145038.aspx). To access BitLocker escrow keys, experts can follow steps described in Microsoft documentation: https://technet.microsoft.com/en-us/library/dn656917.aspx
BlackBerry 10 Forensics
In our original article, we wrote that BlackBerry’s only reason for existence was its exemplary security model. Full-disk encryption, non-bypassable PIN lock and securely locked bootloader all contributed to its security model, rendering JTAG and chip-off acquisition attempts useless.
Immediately after publishing the article we started receiving comments from mobile forensic experts who successfully performed JTAG acquisition of new-generation BlackBerries running BlackBerry OS 10, including Q10 and Z10 handsets. Apparently, there was no encryption to be found anywhere on those devices.
We stand corrected. BlackBerry OS 10 does not activate encryption by default. The user (or the administrator of the corporate BlackBerry Enterprise Server, BES) has to explicitly activate encryption on each device. If it is not enabled, the user partition will be stored in plain, unencrypted form. We have been only working with BlackBerry phones coming from corporate headquarters, and never experienced a single BlackBerry phone seized from a private owner. From our experience, there are very few BlackBerry 10 devices sold to private customers, and we have never encountered one “in the wild”.
Conclusion
As we can see, mobile forensics is indeed a rapidly moving target. The latest version of iOS remained unjailbreakable for much too long, only to be finally jailbroken days after we finished our report. Windows Phone can surprisingly be encrypted with desktop-like BitLocker even though there is no trace of such option anywhere in the phone settings. BlackBerry 10 does not enable encryption by default (who could have thought?), while a newly discovered vulnerability makes millions of Android handsets susceptible to a remote hack. Developers of forensic tools explore new opportunities and add non-obvious acquisition methods, even if for a limited range of handsets. The world is moving so fast these days…
The Tool
Whenever you have a mobile device backup, dump or image, our Evidence Center will help you to quickly find a few hundred of different types of forensically important artifacts, such as mails and calls, chat messages and SMSes, pictures and payment histories. Powerful SQLite viewer will recover deleted items from freelists, journal files and database unallocated space.
Evidence Center does the same quality job with computer and laptop drives or images, what makes it a really versatile tool, able to ease digital investigation both for computer and mobile forensics.
You can request a free full trial license as https://belkasoft.com/trial.
About the authors
Oleg Afonin is Belkasoft sales and marketing manager. He is an author, expert, and consultant in computer forensics.
Danil Nikolaev is Belkasoft sales and marketing manager, co-author, and content manager.
Yuri Gubanov is a renowned digital forensics expert. He is a frequent speaker at industry-known conferences such as CEIC, HTCIA, TechnoSecurity, FT-Day and others. Yuri is the Founder and CEO of Belkasoft, the manufacturer of digital forensic software empowering police departments in about 70 countries. With years of experience in digital forensics and security domain, Yuri led forensic training courses for multiple law enforcement departments in several countries. You can add Yuri Gubanov to your LinkedIn network at http://linkedin.com/in/yurigubanov.
Contacting the authors
You can contact the authors via email:
research@belkasoft.com
Follow Belkasoft on Twitter:
https://twitter.com/Belkasoft
Subscribe to the blog:
https://belkasoft.wordpress.com
Our previous article: Countering Anti-Forensic Efforts - Part 2
All articles by Belkasoft
Trial version of Belkasoft Evidence Center