Belkasoft CTF May 2021: Write-up
The second BelkaCTF was conducted as part of BelkaDay America 2021, a digital forensics and incident response conference by Belkasoft. The CTF started at 11:15am EDT on May 15 and lasted for 24 hours. The official website for the CTF was https://belkasoft.com/ctf_may/ and the tasks were prepared for you by Belkasoft and SPbCTF teams.
This is an official write-up on how the tasks were supposed to be solved. There are naturally more ways to solve these tasks, and we encourage you to read contestants' own write-ups.
Note that every task could be solved without Belkasoft X product, so even if one missed our trial or had any issues with it, it should not have stopped them from giving correct answers.
Let's begin taking flags!
1. Name ('Baby' difficulty)
Question
What is the full name of the phone owner? Format: First Name Last Name.
Solution without Belkasoft X
- There are some WhatsApp preferences in /data/data/com.whatsapp/shared_prefs/com.whatsapp_preferences_light.xml
- See <string name="push_name"> value
Solution with Belkasoft X
- Create a new case and add the .belkaml as a mobile data source
- Analyze the image, selecting all artifacts to be extracted
- Navigate to Artifacts → Overview → Pictures. You can either look through all the pics or run 'Analyze pictures for text'
- Under Overview → Pictures → Text you can find a picture of the X-Ray:
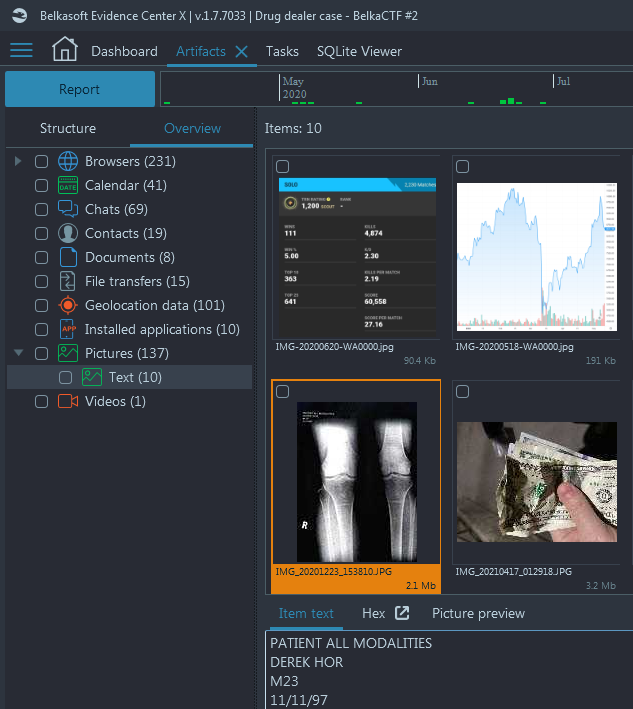
- On the Item text you can see OCR'ed text from this picture, including the patient name, which is the correct answer
Flag
Derek Hor (this task was solved 117 times)
2. Supervisor ('Warmup' difficulty)
Question
What is the phone number he reported to about drug delivery?
Solution without Belkasoft X
- Investigate phone contacts with any tool. The database is stored here: /data/data/com.android.providers.contacts/databases/contacts2.db. The Boss is there and named without any tricks.
- Alternatively, investigate WhatsApp contacts database at /data/data/com.whatsapp/databases/msgstore.db with any tool. Make sure, however, the tool supports SQLite WAL analysis, otherwise you may miss the record because it is stored under so-called 'write-ahead-log' of the contacts database
Solution with Belkasoft X
- Navigate to Artifacts → Overview → Contacts → Find the name 'Boss' and the number is listed within the 'Phone number' column
- Notice that Belka X conveniently shows you both phone contacts and WhatsApp
contacts and that it supports WAL:
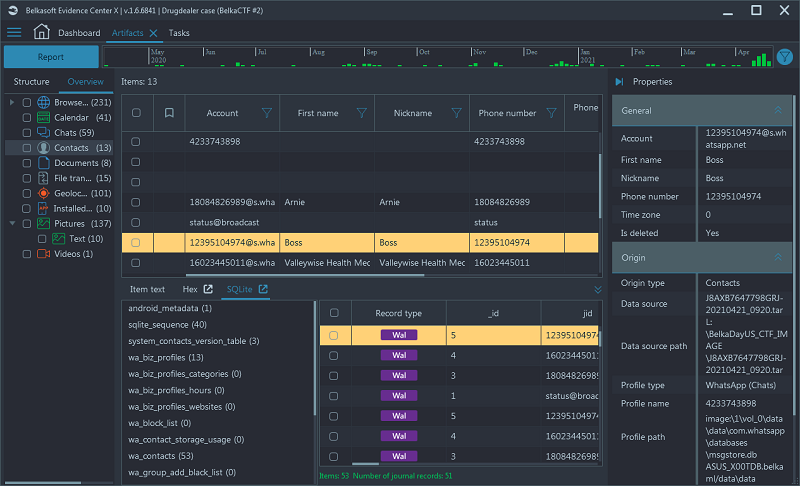
Click to enlarge
Flag
+12395104974 (this task was solved 130 times)
3. Destinations ('Tricky' difficulty)
Question
What were the suspect’s delivery locations on the night of arrest?
Solution with Belkasoft X
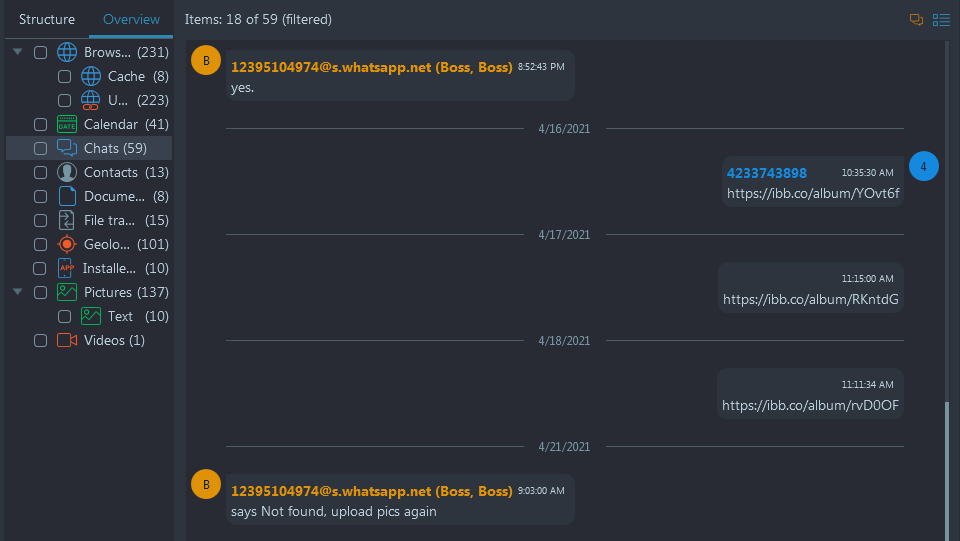
- In WhatsApp there's a clear modus operandi (MO): each day after a delivery,
he sends his boss an album of money exchange photos uploaded to ibb.co—the last
report was on Apr 18th, and the album was https://ibb.co/album/rvD0OF (Navigate
to Artifacts → Structure → Chats → WhatsApp → Filter by Participants, namely by the Boss,
whose contact we already know)
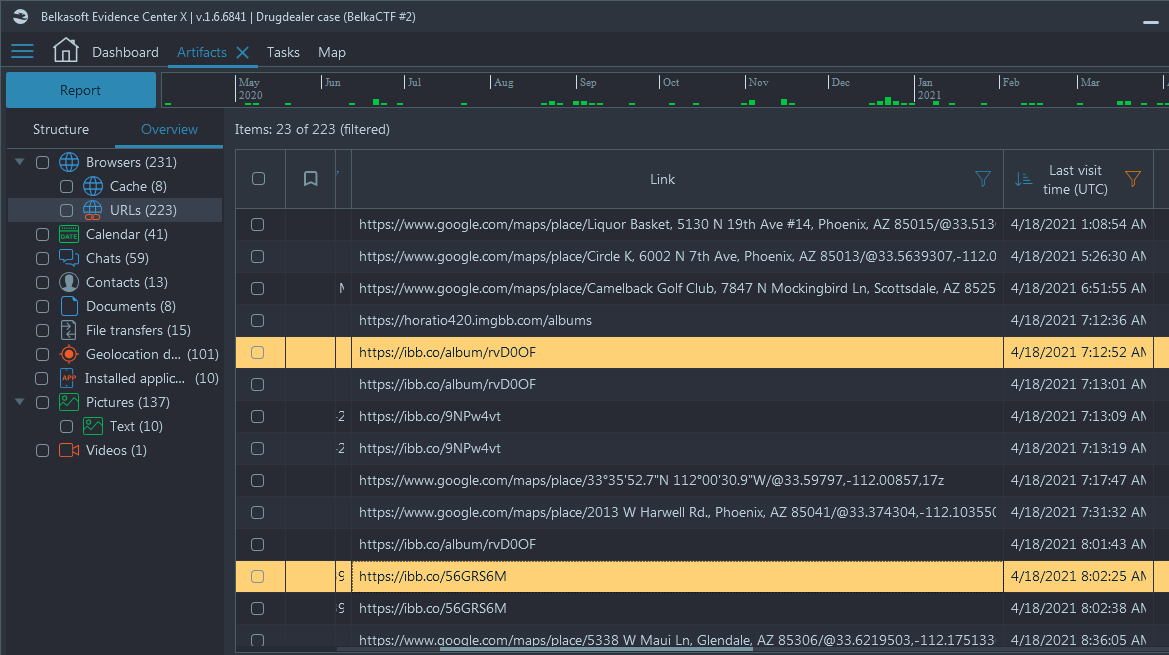
- In Browser history we can see the same pattern: every day he goes to ibb.co
(imgbb.com) to upload individual pictures and adds them to the album of the
day. We see 3 uploads to https://ibb.co/album/rvD0OF from the history, so it
seems like there were 3 delivery locations on that night (Navigate to Artifacts
→ Overview → Browsers → URLs → Sort by 'Last Visit Time Column'):
- In Pictures we can see plenty of money exchange pics, with geolocation data
too (navigate to Artifacts → Overview → Pictures → Filter by 'GPS' & 'Pictures
with GPS'), but not on the night of arrest (Apr 18th):
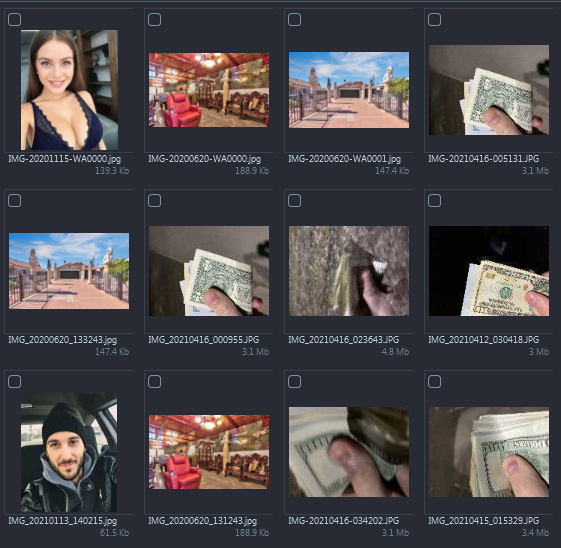
Looks like he switched to taking photos right from ibb.co upload page so we cannot extract GPS info from here - In Browser history we also see frequent Google Maps usage, looking up different locations. If we check previous days, we see that photos locations are the same as locations googled right before ibb.co image upload. So it looks like he googles a spot, travels there, hands in the drugs and snaps a pic of money exchange, uploading it to ibb.co (Navigate to Artifacts → Overview → Browsers → URLs → Sort by 'Last Visit Time Column' → Filter on 'Page Name Column' for 'Map')
- Now putting it all together, from Browser history we need the locations
googled prior to the 3 uploads on the night of 18th:
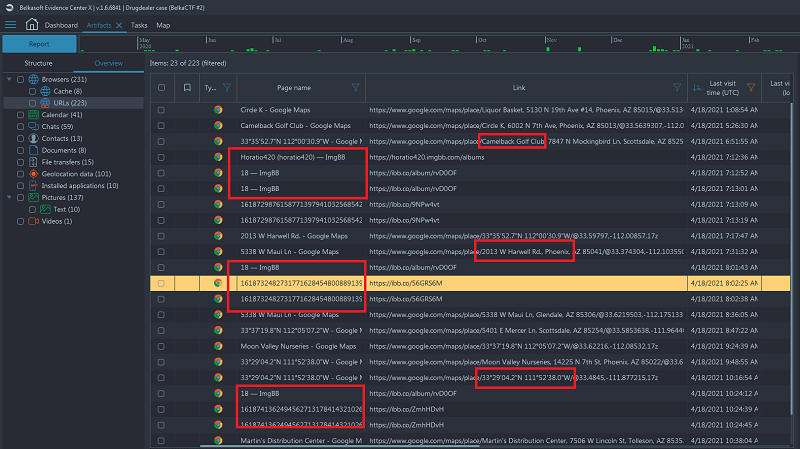
Solution without Belkasoft X
- It is anticipated that you can repeat similar actions with another tool or manually going through databases mentioned in the solution with Belkasoft
There is a catch by the way: Google Maps acts weird in browser history, and actually shows a future webpage Title near the real URL. You need to determine places based on URL, not the title.
The benefit of using Belkasoft X here is that it helps to get the geolocation data directly from Google Maps app. You can also review geolocated data on a map: Artifacts → Overview → Geolocation data (right click) → Show on map.
Flag
Camelback Golf Club, 7847 N Mockingbird Ln, Scottsdale, AZ (33.5542226,-111.9340928)
2013 W Harwell Rd., Phoenix, AZ (33.374304,-112.1035501)
33°29'04.2"N 111°52'38.0"W (33.4845,-111.877215)
4. Job Experience (Baby)
Question
How long has the suspect been acting as a drug dealer?
Solution with Belkasoft X
- We can presume that the night of his arrest is April 18th, 2021 due to the
activity present on the user's device. The last user event was the picture sent
with a link to the ibb.co album displaying the picture of the money collected.
This can be viewed by looking at the Timeline window of Belkasoft X (Navigate to Timeline
→ Sort by any 'Time' column and look for last user event)
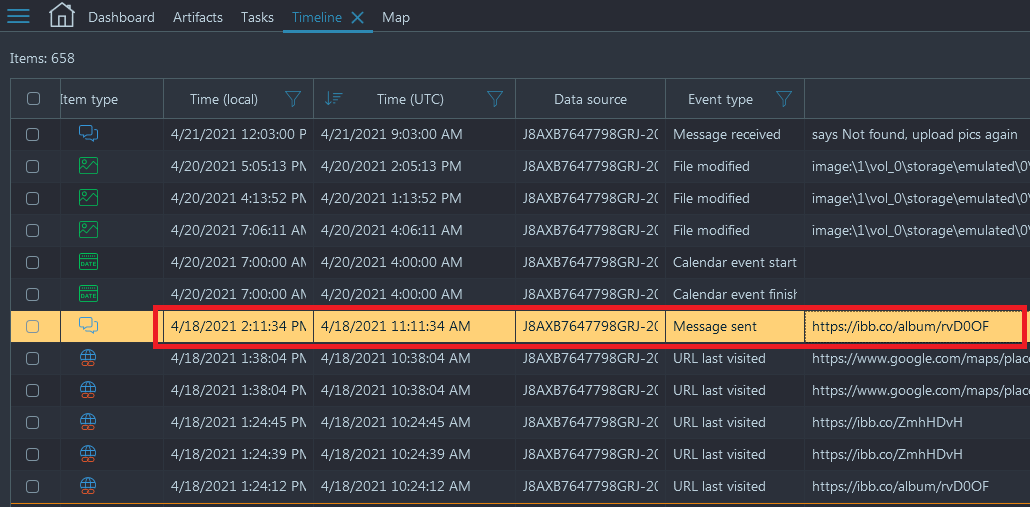
- Now, the only way to know when he started working, would be to reference
some sort of communication or event that would seem to fit. After navigating
through the system image, we find reference to a chat between Derek and Arnie
regarding an Interview on June 20th, 2020 (Navigate to Artifacts → Structure
→ Chats → WhatsApp → Filter for 'Interview')
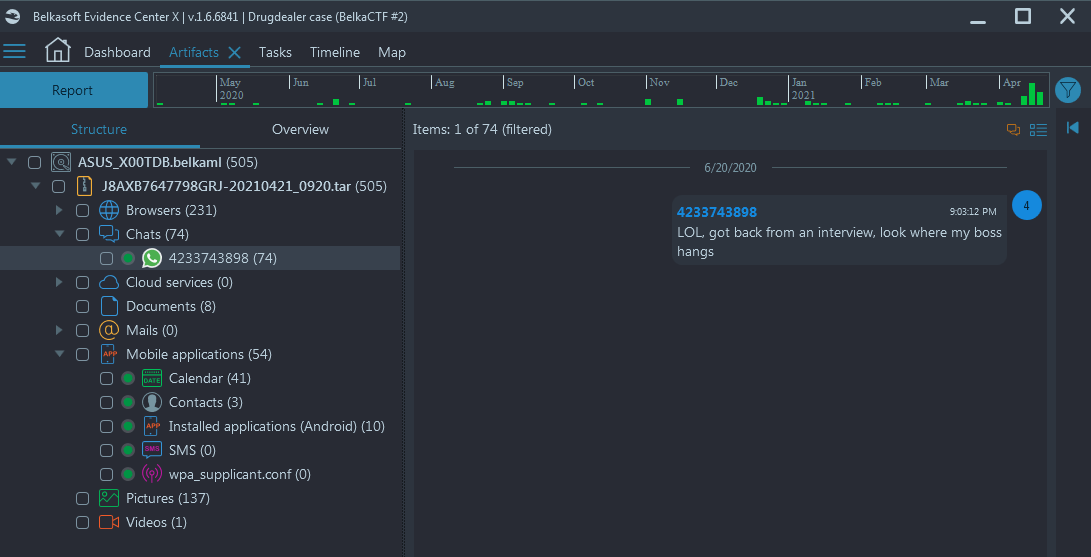
- So now we see an interview on June 20th, 2020 and an arrest date of April 18th, 2021. If we navigate to https://www.timeanddate.com/date/duration.html and enter those dates (To include the date of the arrest) we get the flag
Solution without Belkasoft X
- The logic is the same
Flag
303 days (this task was solved 53 times)
5. Salary (Tricky)
Question
From what Bitcoin wallet did he get paid the last time for his job?
Solution with Belkasoft X
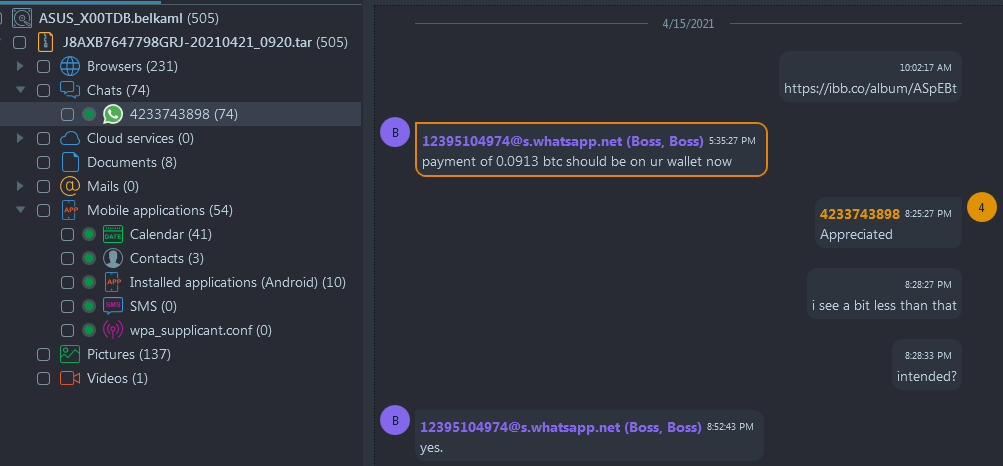
- The WhatsApp messages give us a hint as to how much Bitcoin was sent for services on two occasions
- First transmission with known tx hash was in March and it is not the latest
- The second one is in April and it mentions an amount and then the message 'I see a bit less
than that' (Navigate to Artifacts → Structure → Chats → WhatsApp → Filter
by Participants ('12395104974@s.whatsapp.net (Boss)')
- The next step involves us doing a search on
https://blockchair.com/bitcoin/outputs
(or a similar service) where we have to enter the evidence that we do have.
We can filter by the date and time (April 15th, 2021 between 17:20 and 17:40)
as well as the range of bitcoin value (0.0913 and around; note: blockchair operates on BTC sums in satoshi
so 0.0913 is 9130000). This will give us
the output of only one transaction that took place within those set parameters.
Following that transaction link gives us our flag:
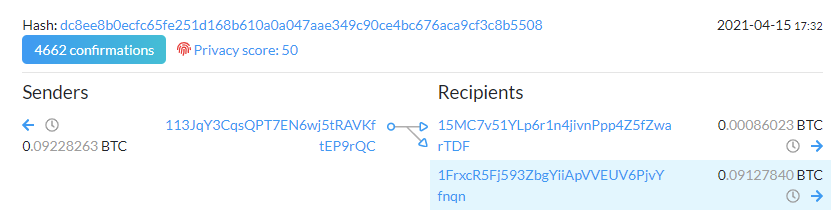
Solution without Belkasoft X
- The logic is the same
Flag
113JqY3CqsQPT7EN6wj5tRAVKftEP9rQC (this task was solved only once, tricky indeed!)
6. Supplier (Hard)
Question
What is the phone number of the drug supplier?
Solution with Belkasoft X
- There is nothing within the image that directly gives us the supplier's phone
number, but we do see that the application 'Signal' is installed on the device.
We can go to the File System and recover a Signal backup (Navigate to File System
→ data → media → 0 → Signal → Backups → signal-2020-12-20-21-04-59.backup)
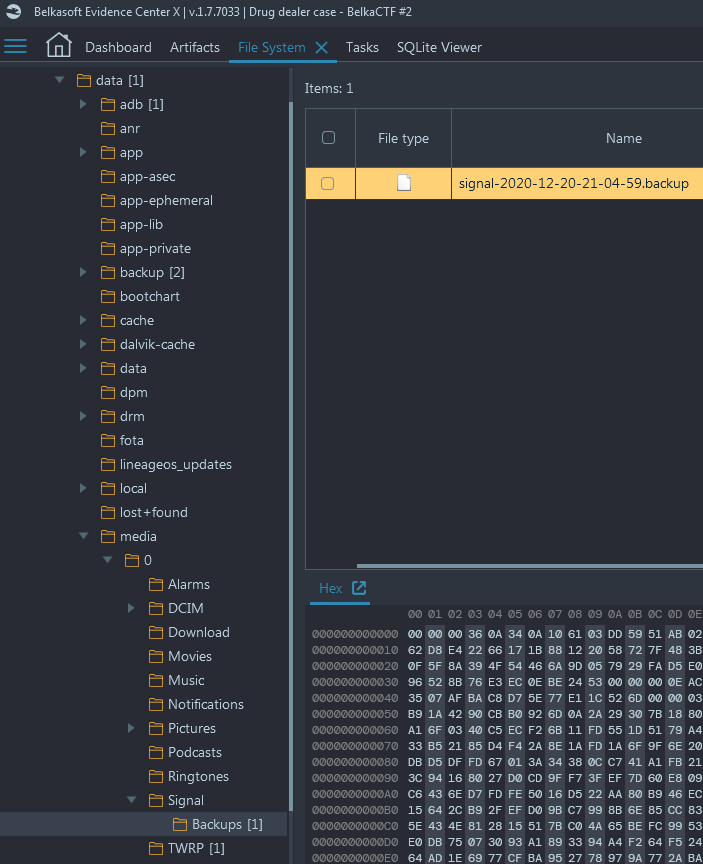
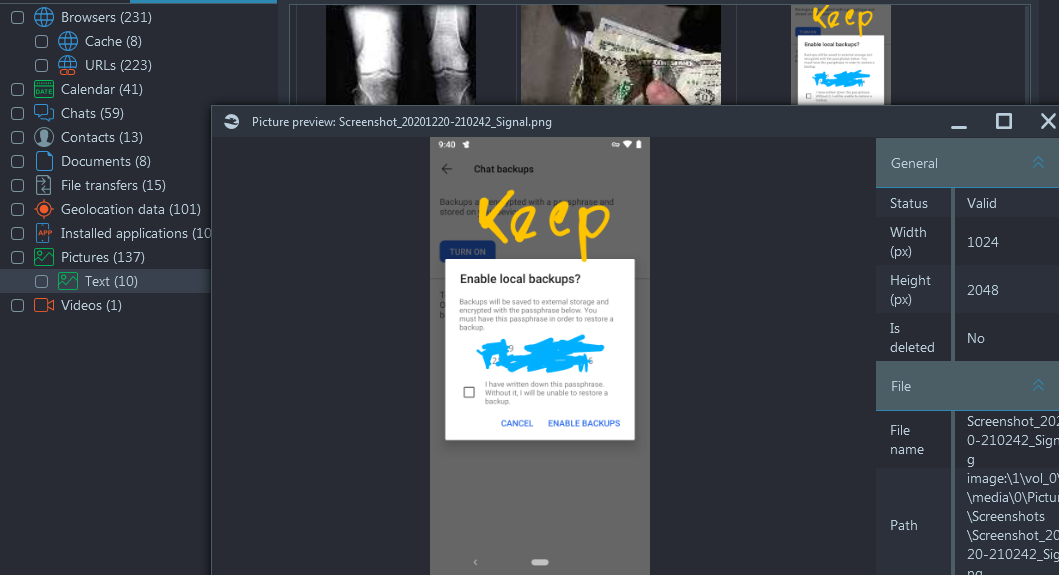
Actually, when you analyze the image, Belka X asks you about the password for this Signal backup, in its Tasks window - Now we need a password to decrypt the file. While navigating the device
we see a picture of a screenshot
that has a password with scribbles on it that also have the word 'Keep' (Navigate
to Artifacts → Overview → Pictures)
- In Installed Applications we also see that there's a note application installed: Google Keep - Notes and Lists
- The word 'Keep' on this image is the next clue to decrypt the Signal backup.
The user stores the backup password within Google Keep. While traversing the
device, we do see that Google Keep is installed on the device. Lets get the
SQLite database for Google Keep and see if we can grab the password to decrypt
the backup (Navigate to File System → data → data → com.google.android.keep
→ databases → keep.db)
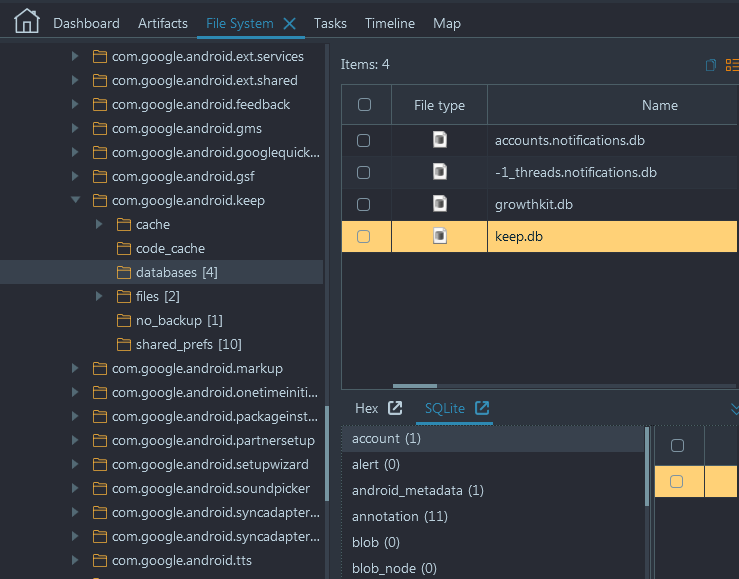
- Next, we open the SQLite Viewer within Belkasoft X while having the keep.db
selected. Browsing the database in the SQLite Viewer we stumble upon a password
that looks similar to the one we were given during the challenge on the CTF
website (the screwup). It is located under 'text_search_list_items_content'
and the value is: '04049 19810 47697 72485 91554 88046'
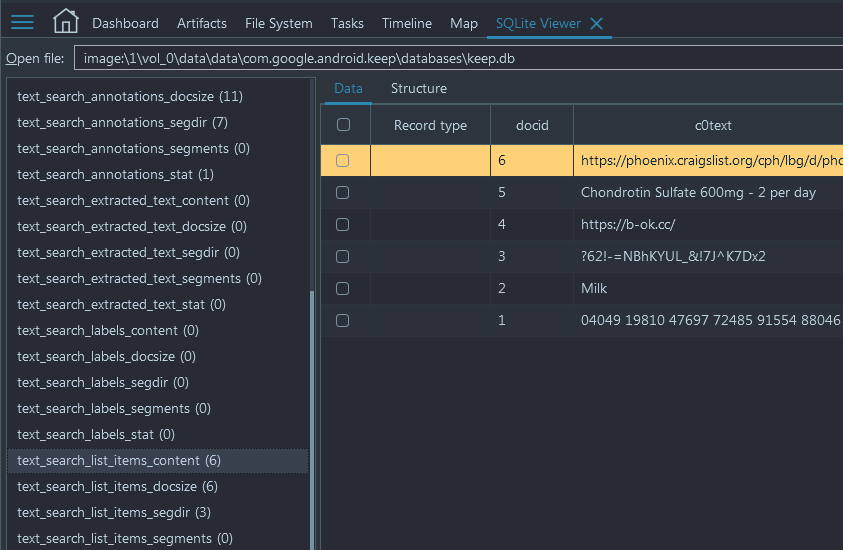
- Now, to get contacts, proceed to Artifacts → Overview → Contacts and
filter by the Signal profile. You will see these three contacts:
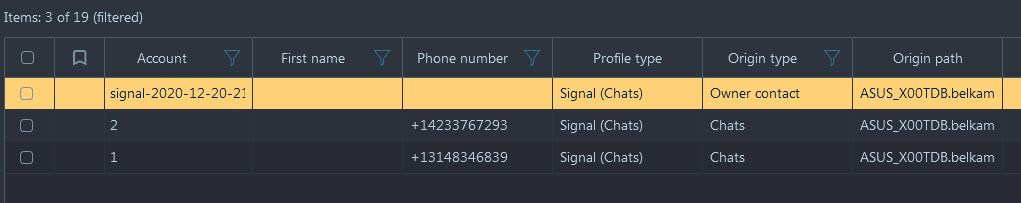
You need the contact number two.
Solution without Belkasoft X
- After locating the Signal backup (manually) and the password (any SQLite
viewer, this time you do not need WAL or freelist support),
you can use an open source tool
https://github.com/pajowu/signal-backup-decode
as follows:
/root/.cargo/bin/signal-backup-decode --password '04049 19810 47697 72485 91554 88046' signal-2020-12-20-21-04-59.backup - The tool creates an SQLite database with the extracted data. In the 'recipient' table we see two phone numbers: +13148346839 corresponding to profile name horatio0.42k (it's Derek Hor), and +14233767293 which is our target supplier
Flag
+14233767293 (this task was solved 35 times)
7. Refill (Tricky)
Question
When was the last time the suspect met his supplier? Provide exact timestamp in a common format, e.g. 2021-07-17 17:07:07 UTC
Solution with Belkasoft X
- This time we can use the Signal message history extracted by Belka X. There we see that there was a meeting planned for Dec 17th at 2 PM, and the planned location was 33.508136, -112.148462
- Alas, this was not the last meeting with supplier. False lead! Well, almost...
- If we look at the Calendar, we can find 33.508146, -112.148462 location for one of the events, for 2020-12-17 21:00:00 UTC (it is 2pm Phoenix time)
- Select this event and switch to SQLite view of the Calendar. The title of
the event is 'Pizza delivery':
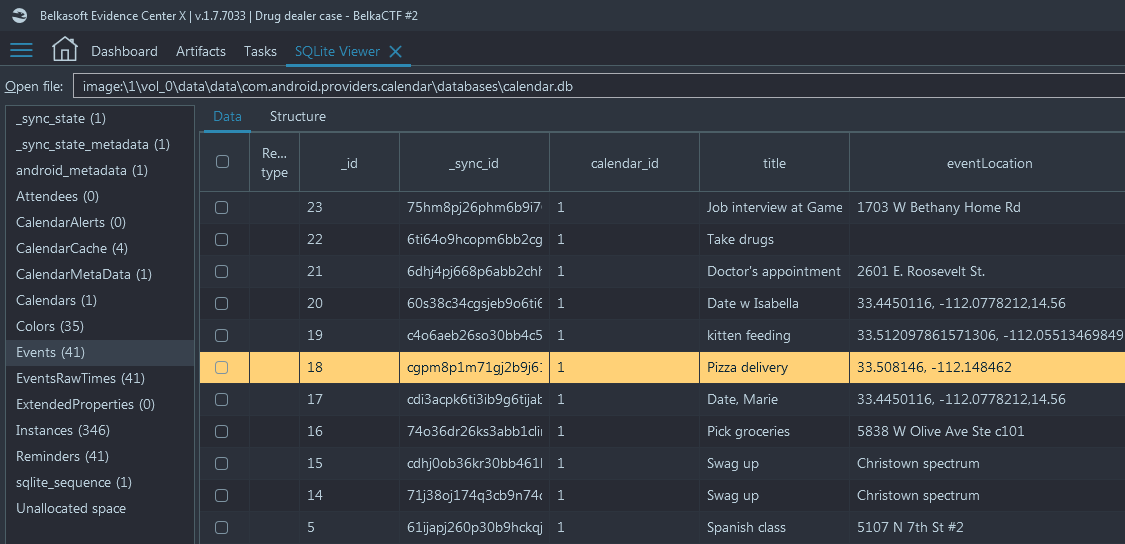
At this point we have all the reasons not to think he is a pizza delivery guy. This is actually another modus operandi of the dealer: for supplier meetings he uses 'Pizza delivery' as a calendar codeword - Let us try to find the most recent Pizza delivery in his calendar. In Belka
X's SQLite Viewer you can sort by any column; so sort the 'Events' table by the
'title' column and find out the 'Pizza delivery' with the biggest '_id' value.
It is id number 36:
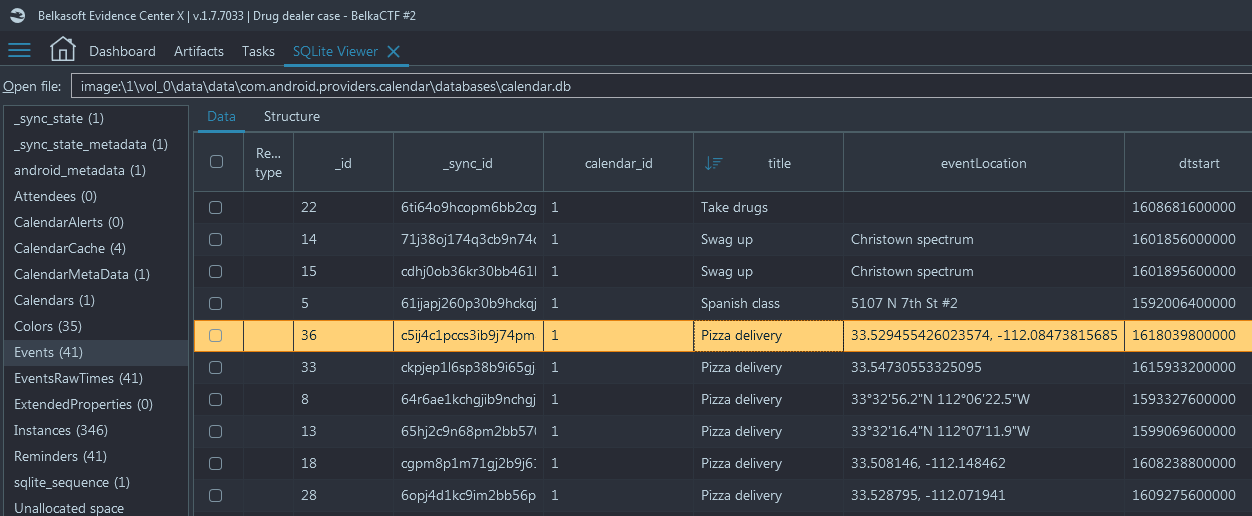
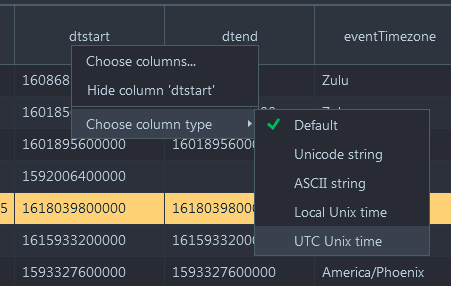
- Now, right click on the 'dtstart' column which corresponds to the event
start time and select 'Choose column type'. Belkasoft X can convert column values
to different formats, select UTC time:
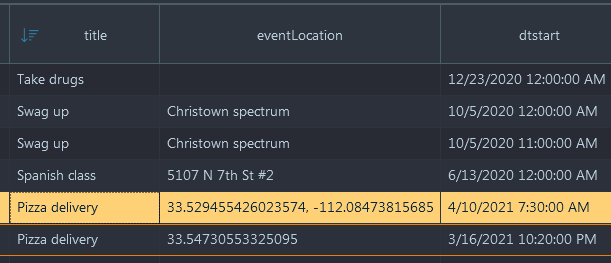
- Now, Belkasoft X shows you the correct answer:
Solution without Belkasoft X
- The same logic and any SQLite viewer will help you to solve the task. This time, SQLite viewer does not necessarily have to support forensic features, so 'DB Browser for SQLite' will do
- For time conversion, use any online converter or the DCode tool
Flag
Sat, 10 Apr 2021 07:30:00 UTC (this task was solved 22 times)
8. IMEI (Warmup)
Question
What is the supplier's phone IMEI identifier? Help yourself to the NSA metadata storage: cellrecordslookup.nsa.fyi
Solution with Belkasoft X
There is no anticipated solution with Belkasoft. However, Calendar events extracted by X will help. You already have all events named 'Pizza delivery' showed next to each other in the SQLite Viewer of X (and we know he is not a pizza delivery guy). Extract all locations from these events, they are six, and converted times as shown in the previous task:
Sun, 28 Jun 2020 00:00:00 -0700 33°32'56.2"N 112°06'22.5"W
Wed, 02 Sep 2020 11:00:00 -0700 33°32'16.4"N 112°07'11.9"W
Thu, 17 Dec 2020 14:00:00 -0700 33.508146, -112.148462
Tue, 29 Dec 2020 14:00:00 -0700 33.528795, -112.071941
Tue, 16 Mar 2021 15:20:00 -0700 33.54730553325095 (bad location)
Sat, 10 Apr 2021 00:30:00 -0700 33.529455426023574, -112.0847381568517
Now, proceed to 'Solution without Belkasoft X'.
Solution without Belkasoft X
- For this task, we were given an 'NSA' tool that allows us to look up cellphone registration history. When we look at the tool, we see we need a latitude, longitude, and a date in (MST). Now we must enter the data. Take the data extracted from the Calendar automatically by Belkasoft X or manually by yourself
- Feed every line into the lookup tool. You will get the output of the number of devices found with their IMEIs. Copy the list of IMEIs into an Excel spreadsheet. You can intersect all the lists by duplicates search (meaning that an IMEI was found in more than one location). Just two IMEIs will be common for all the locations, they are 350236009513272 and 332182208414842. One of those is Derek, the other is the supplier
Note: Are you sure this is a real NSA tool?
Flag
332182208414842 (this task was solved 11 times)
9. Not The End (Surprise task)
Well, this was just a fun task, which opened 30 minutes before the end of the competition. To score, one had to click on any 'social share' link at the bottom of the task box. We deliberately did not check if an actual post was made, so it was easy to cheat :). We hope, however, that those who enjoyed solving the CTF will share their thoughts voluntarily. Your posts motivate the team, that's our reward!
Please do not forget to use the #BelkaCTF hashtag.
Flag
flag{7hank5_f0r_pl4y1ng_and_s33_y4_n3xt_t1me} (this task was solved 31 times)
So what's next?
We will have the second part of this story in June, 2021, and this time you are going to meet The Boss, mentioned in the just finished CTF tasks. Surprise: we will have two set of prizes for the #BelkaCTF number 3: one for the individual CTF winners and the other one for overall winner, who gets maximum cumulative score, summing CTF#2 and CTF#3. Do not miss the next CTF as your score from the first half will help you a lot to compete for the grand prize!
Here is The Boss by the way:
